For the second year in a row the World Economic Forum lists cyberattacks as one of the top five global risks, and highlights that an attack on a country’s electricity system could potentially have devastating effects. Power grid risk has increased due to expanded connectivity to IT and other systems, exposing them to more threats. As the same time, threat actors are focusing more on critical infrastructure attacks, and benefiting from the availability of malware toolsets on the internet.
Unfortunately, defending today’s power systems is challenging because they typically use communication protocols optimized for bandwidth and efficiency, with zero or simple security protections. Furthermore, many grids have received little to no security enhancements post deployment.
To help counter this problem, in the early 2000s IEC Technical Committee 57, a group devoted to power system management standards, started working on how to make power grids secure-by-design. Working Group 15 (WG15) was formed to evaluate the requirements from a technology perspective, and define a standard way to implement them.
I’ve been a member of WG15 since 2015, and led the Nozomi Networks hosting of the WG15 Winter ’17 meeting in Lugano, Switzerland. As we approach the group’s next meeting this spring, I thought it might be helpful to inform you about these standards and provide an update on their status.
Overview of WG15
First a brief overview of WG15. The group is made up of ICS operators, SCADA engineers, security specialists, and networking experts from 90 organizations worldwide. Members include ABB, Siemens, Schneider Electric, General Electric, Enel, IREQ, Nozomi Networks and others.
Together we have identified the components needed for a secure-by-design power system. These include the end-to-end encryption principle, the definition of roles for all users and identity management, and pervasive monitoring of the system itself.
Another duty of WG15 is to review other Working Group’s documents to assess and validate cyber security aspects.
Status of the IEC 62351 Standards
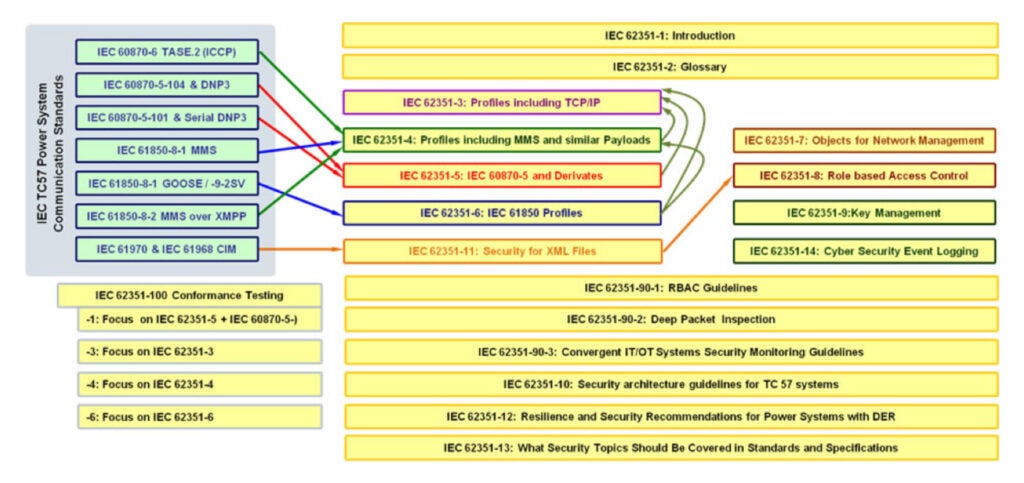
Currently, the 62351 family of standards (see IEC 62351-1: Introduction for an in-depth overview) depicts the architecture of a secure power system and standardizes its protocols and components. An interesting read for a better overview of it is: IEC 62351-10: Security Architecture Guidelines for TC57 Systems.
To truly obtain effective end-to-end security, secure protocols must:
- establish secure connections based on some trusted private key of the actors, and
- have a repository of actors allowed to act inside the system.
The former is standardized in IEC 62351-9: Key Management, while the latter is standardized in IEC 62351-8: Role-based Access Control (RBAC), and further reviewed and explained in IEC/TR 62351-90-1: RBAC Guidelines.
Communication protocols play a key role when it comes to resolving “common OT protocol issues”, such as the lack of authentication, integrity checks, confidentiality, etc. Although some OT protocols already address these areas, it is very common within the OT world to have very low “protocol security”, that is insecurity-by-design. For this reason, the whole set of power system protocols designed under the IEC umbrella has been extended to provide end-to-end encryption, identity management and RBAC.
Of course, the role of existing secure protocols like TLS (Transport Layer Security) play a big role, but many other aspects have been tackled to define all possible facets of a secure architecture. These include:
- Using certificates for all devices
- Standardizing how to behave with rare long-standing TLS sessions
- Creating completely new encryption sub-protocols for specific use cases
Monitoring Power Systems with IEC 62351 Standards
In the IEC 62351 family of standards, end-to-end encryption is certainly an important feature, but system monitoring plays a key role as well. Several parts are in fact devoted to monitoring the healthy status of a power system:
- Part 7 (IS, International Standard) is focused on the active monitoring of IEDs and other power system components. A generic approach (via UML) has been used in the standard to define what needs to be monitored. Additionally, a pragmatic SNMPv3 mapping profile is provided for monitoring a dedicated set of MIBs (Management Information Bases).
- Part 14 (in draft right now) is focused on the logs that power system components should generate. Standardizing the format and the semantics helps lower the cost of implementation and maintenance of power grid log management solutions.
- Part 90-2 (TR, Technical Report) is focused on how Deep Packet Inspection (DPI) of IEC 62351 encrypted channels can be carried out. The document explains the state of the art of existing DPI techniques and how they can be applied to monitor IEC 62351 channels today. It is also the reference work for analyzing changes to apply to protocols and technologies to enable easier and more secure DPI of communications.
A lot of discussion has occurred on this topic because of its controversial nature. Nonetheless, deep monitoring of encrypted communications in a machine-to-machine framework offers more advantages than not, including full visibility of ongoing activities.
- Part 90-3 (in draft right now) is focused on putting the three parts above together. It aims to provide practical examples of how to monitor a power system in order to obtain deep visibility and support forensic analysis, consequently enabling a more dependable and resilient system.
Nozomi Networks is Committed to Securing OT Systems
I hope this brief overview of the IEC 62351 family of standards, starting from its foundational goal and focusing somewhat on its monitoring aspects, is helpful. Even though these standards are specific to power systems, they are often used in other domains, such as gas distribution. As such, they provide a good idea of the components needed for secure ICS communications.
Nozomi Networks is very committed to securing OT systems and we believe that standards for secure communications are important. That’s why I’ve been involved with WG15 and have contributed to the development of the standards, particularly sections related to power system monitoring (reviewing Part 7, leading Part 90-2 and now Part 90-3).
In my next installment on this topic I’ll go into more detail on the IEC 62351 monitoring standards, including their different options and how to take advantage of each of them.
Reference List of IEC 62351 Standards:
- Iectc57.ucaiug.org: Public Information on WG15 IEC 62351 Standards and Activities
- IEC/TS 62351-1: Introduction
- IEC/TS 62351-2: Glossary of Terms
- IEC 62351-3: Security for profiles including TCP/IP
- IEC 62351-4: Security for profiles including MMS
- IEC 62351-5: Security for IEC 60870-5 and derivatives
- IEC 62351-6: Security for IEC 61850 profiles
- IEC 62351-7: Objects for Network Management
- IEC 62351-8: Role-Based Access Control
- IEC 62351-9: Key Management
- IEC/TR 62351-10: Security Architecture
- IEC 62351-11: Security for XML Files
- IEC/TR 62351-12: Resilience and Security Recommendations for Power Systems with DER
- IEC/TR 62351-13: Guidelines on What Security Topics Should Be Covered in Standards and Specifications
- IEC 62351-14 Security Event Logging and Reporting
- IEC/TS 62351-100-1: Conformance test cases for IEC 62351-5 and companion standards
- IEC/TS 62351-100-3: Conformance test cases for IEC 62351-3
- IEC/TS 62351-100-4: Conformance test cases for IEC 62351-4
- IEC/TS 62351-100-6: Conformance test cases for IEC 62351-6
- IEC/TR 62351-90-1: Guidelines for Using Part 8 Roles
- IEC/TR 62351-90-2 Deep Packet Inspection
- IEC/TR 62351-90-3 Guidelines for Network Management










