The massive presence of unprotected IoT devices is providing many opportunities for malicious threat actors. Most of these devices are plug-and-play and do not require any kind of configuration, making security optional.
In fact, manufacturers ship the devices with default passwords that are publicly known, providing easy access to the configuration panel for new users. If such passwords are not replaced with new, strong ones, they provide the first entry vector used by attackers.
Attackers who compromise a high number of IoT devices usually create botnets to trigger DDoS (distributed denial-of-service) attacks with the goal of disabling systems for hacktivism or financial gain.
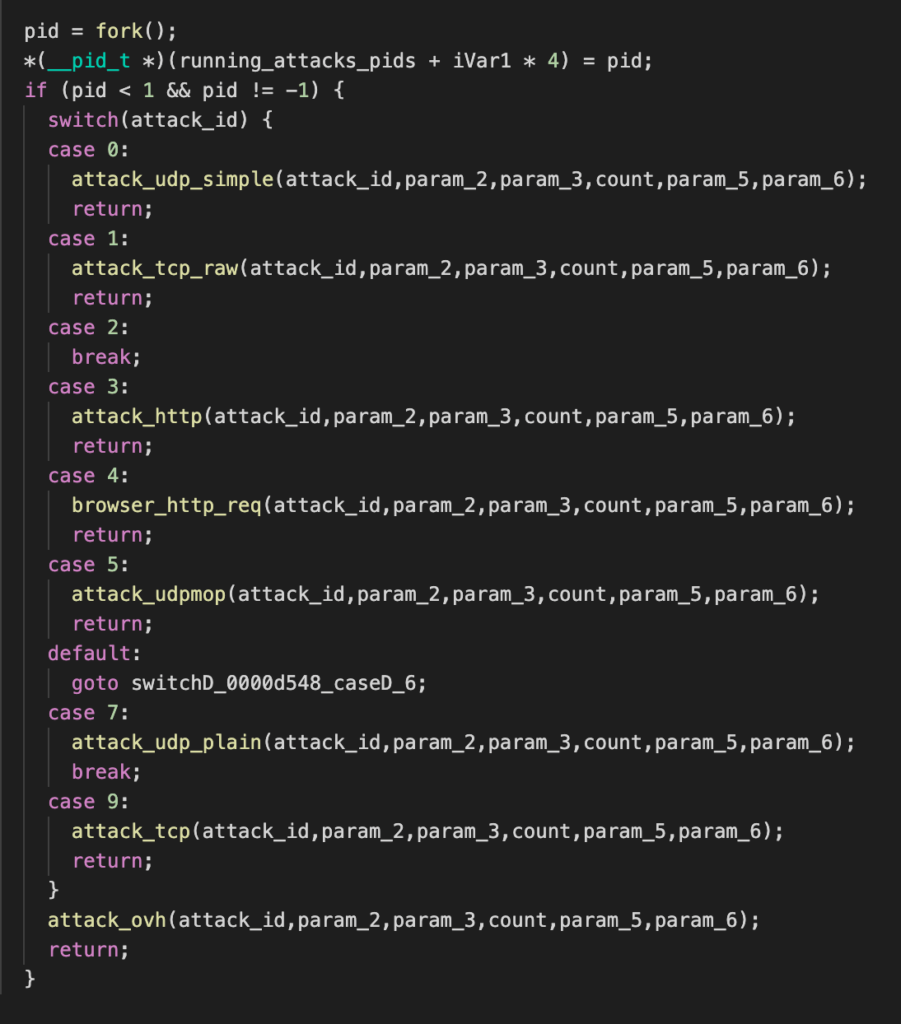
Our team of security researchers at Nozomi Networks Labs analyzed several variants of the IoT botnet dubbed Dark Nexus. It is a new IoT botnet that has come to prominence in the last few months and its capabilities have been thoroughly discussed by Bitdefender researchers. [1]
We analyzed its network behavior, which we describe in this post, and provide a detection signature to help protect IoT, OT and IT networks.
IoT Botnet Dark Nexus: Three Categories of Network Activity
The Dark Nexus bot leaves a hefty network trail that can be broadly divided into three categories:
- C&C (command and control) communication
- Self-propagation
- DDoS attacks
Though self-propagation and DDoS attacks could be a single category, their final goals are very different, so we prefer to analyze them separately. To properly commandeer the bot in our lab, we wrote a replacement for the C&C server that allowed us to trigger network activity in a controlled manner.
While the bot carefully analyzes the system it is executing in, and kills suspicious processes that might hinder its activities, the most delicate section remains the network parsing code. This is a critical feature for a botnet, since a bug in this area might lead to catastrophic consequences for the threat actor. The botnet itself could become vulnerable to DDos attacks or be completely taken over by a different hacking group.
We analyzed each of the three categories of Dark Nexus’ activity.
C&C Communication Aims to Download Latest Version
Once a device is infected, it performs a GET request to retrieve its IP: