This week IoT security camera provider Verkada was the target of a successful cyberattack that allowed the perpetrators unfettered access to the live video feeds of 150,000 surveillance cameras. The shock of seeing images from inside hospitals, jails and manufacturing facilities brought home the risks involved in leveraging IoT devices for legitimate business purposes.
Most of the victims of this attack only found out about it when images of their facilities were shared over the internet. That’s unfortunate because network monitoring technology is available today that can alert organizations to such attacks as soon as they occur – and help them contain and mitigate its impacts.
Let’s take a look at what happened with this attack – and how defenders could have prevented its damaging outcomes.
The Verkada Security Camera Breach – What Happened
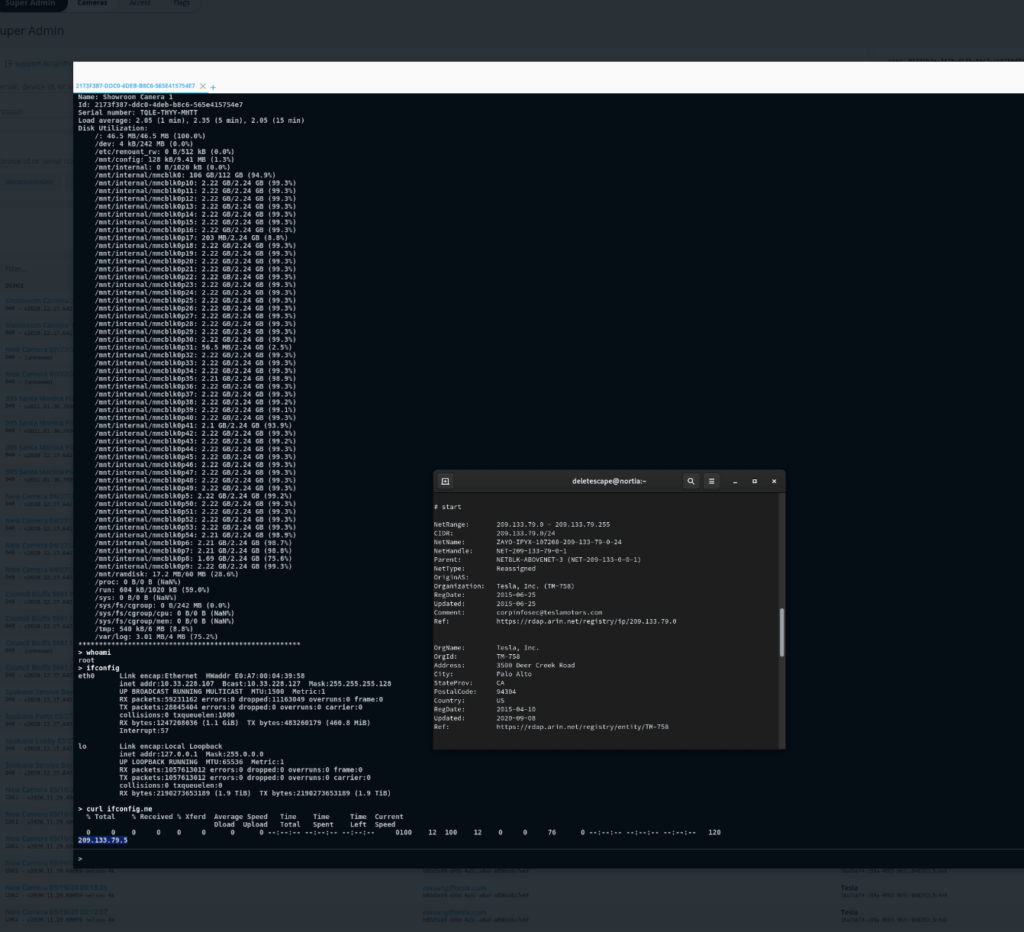
After the Verkada attack was made public, technical details provided by the vendor indicate the attackers gained access to an internet-exposed server used by its support team to carry out maintenance operations on customer cameras. Within this system, the intruders gained privileged account credentials that eventually allowed access to surveillance cameras deployed at thousands of customer sites.
In addition to acquiring the video streams, the attackers were able to execute shell commands on the breached cameras. This is particularly worrisome because it’s unlikely that all Verkada customers deployed the devices in a perfectly secured Zero Trust environment.
Although the vendor declared that all the shell commands issued through the internal tool were logged, from the point of view of a breached end user, this information might not be enough to investigate the situation. It’s always difficult to predict what an advanced malicious actor, with a specific plan in mind, can come up with.
Furthermore, it’s pretty common to anybody with some red team experience to prepare an engagement where the only entry point within an organization is represented by a shell on an IoT device. In these scenarios a popular option is to upload the tools required for lateral movement on a third-party website, then download the tools and run them from the IoT device, based on the specific needs.
The other important factor here is the timing. Reacting quickly to an incident, as soon as your systems detect the first evidence, is becoming more important than ever. We’ve seen several attacks where the threat actors simply don’t care about being detected later on, as long as their goal was achieved.
Behavior-Based Anomaly Detection of IoT Devices is Key
The Nozomi Networks research laboratory contains many devices from many vendors. They are used in a wide variety of sectors and communicate using a diverse set of protocols. Having access to such a varied network of physical devices allows us to improve our products’ understanding of individual protocols and their behaviour. With the assumption that some of these devices can potentially display hostile behavior, we take measures to carefully isolate them in the network, while at the same time providing a realistic test bed for research.
One of the devices, which is part of an isolated IoT network, is a Verkada D40 camera. As shown below, the Verkada camera interacts with several different external hosts to provide functionality such as regular firmware updates, remote access to the video feed and maintenance operations.

While the operation of IoT devices is most often opaque, monitoring their network behaviour with anomaly detection provides much-needed alerts that highlight unusual behavior.
In this case for example, a network learning system would understand that communication with api api.control.verkada.com and index.control.verkada.com over HTTPS is expected for this device and use that as a behaviour baseline. If an attacker were to remotely access a shell running on the device through the vendor’s interface, any action they then take would deviate from the established baseline and flagged as an alert.
With the goal of further compromising the target network using the camera as a launchpad, an attacker would have to perform reconnaissance to better understand the target. This would involve activities such as port scanning or credential guessing against hosts inside the local network. Both are clear deviations from the device’s established baseline behaviour and would generate timely anomaly alerts.
With IoT devices, to reduce anomaly alerts to those that precisely pinpoint incidents truly needing attention, it’s important for the monitoring solution to receive regular device profile updates. The Nozomi Networks solution, for example, includes an Asset Intelligence service that ensures accurate anomaly alerts.
Deploy Network Monitoring Before Deploying IoT Devices
Detecting post-infection nefarious activities is fairly trivial with network monitoring technologies. In the spirit of the Zero Trust model, it’s important to recognize that today we’re discussing Verkada, but tomorrow it will be a new vendor, and yesterday was a different attack. Knowing that, the importance of having independent and reliable, cybersecurity monitoring technology, already in place, is crucial to managing the risks posed by the mere existence of technologies.
Having monitoring in place before an incident happens can mean the difference between fully recovering, and not. If simply patching up the infected devices without tracing the rest of the attackers’ footsteps is the response plan, it will likely lead to multiple remediations. Operators will likely have to disinfect and attempt to remove malicious code again, from another part of their enterprise.
Knowing the following is as important as identifying the initial actor vector:
- Reconnaissance activities – what the attackers searched for
- Lateral movement – where they navigated to
- Persistence – what other systems they may have breached
- Exfiltration – what data was compromised or downloaded
Not having these types of records severely impacts the recovery efforts.
In a Zero Trust model, using a cybersecurity monitoring system to watch for signs of infection could have reduced the impacts to some of Verkada victims. For example, one publicly known victim became aware of their infection only after it was revealed in posts on Twitter. Had behavior monitoring and anomaly detection been in place before infection, the company’s cybersecurity team would have been alerted on initial connection attempts from the infected device. This would have provided them with the opportunity to respond before the attackers were able to do any further damage.
IoT Security Camera Breach Shows Need for Network Monitoring
This attack on Verkada’s security camera systems did not involve a sophisticated threat actor or cunning attack techniques. It was the result of a curious group finding privileged credentials on the open internet. This lack of security hygiene is unfortunately not atypical when it comes to the wide variety of IoT devices in use and being purchased today.
We urge you to prepare for inevitable breaches by strengthening your cyber resilience.
To find out more about the Nozomi Networks OT/IoT network monitoring and security solution, contact us.
References:
“Latest Security Update”, Verkada, March 10, 2021.










