In OT and IoT environments with no industrial control systems (ICS) security measures, it can be extremely easy for a threat actor to disrupt operations. Though new weaknesses like zero-day vulnerabilities are being identified every day, the most common avenue of disruption is to exploit bad practices and misconfigurations. Situations caused by human error or a lack of security procedures – which are preventable with proper assessment and care – are often the main culprits exposing industrial operations to hazardous scenarios.
We constructed a simplified production line to illustrate how easily the industrial process can be disrupted. With a simple DoS (Denial of Service) script that could be introduced by any hacker, the process can be put into a fail-safe state, freezing the entire production line. What needs to be emphasized is that an attack like this is easy to prevent if the industrial switch is configured from a security-oriented approach, and if defense-in-depth best practices are used.
Let’s look at a physical demonstration that shows the link between functional safety and ICS security, and review what can be done to prevent malware from disrupting production and threatening safety.
Industrial Control Systems Are Easily Disrupted
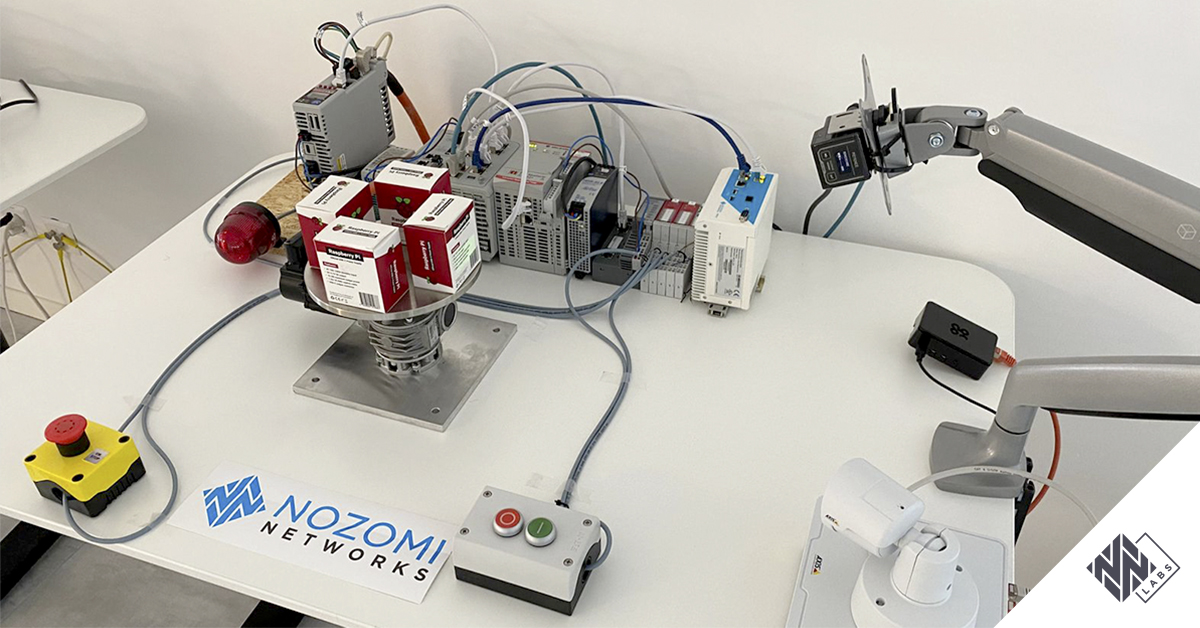
Our simplified production line consists of a barcode reader and a table rotated by a servo motor. Every time the reader successfully scans a barcode, the table rotates so that the next barcode can be scanned, simulating a production belt. If the barcode reader fails to read a code, the motor will not initiate a move until it has succeeded.
Both the motor and barcode reader are controlled by a single PLC, with I/O controls to start and stop the process. We also introduced a safety function with an E-stop button that, when pressed, halts the process and triggers an alarm light. The system has a dedicated VLAN along with the operating systems that control the entire process.
In our simulated industrial process, the single PLC controls both the main process described above and a secondary safety function. This safety function is a common requirement in Safety Instrumented Systems (SIS) to handle any hazards that could occur if the primary process fails. By splitting the functions into two different systems, the functional requirements are separated from the safety requirements. This separation creates some redundancy between the safety function and main function in the PLC. It’s not uncommon to use separate devices for these two functions, such as two PLCs.
In this scenario, the safe state is the activation of the Safe Torque Off (STO) to the motor, which is a basic drive-integrated safety function. It ensures that no torque-generating power will be sent to the motor, preventing unintentional starting. Without such a feature, the inertia and friction forces of the system would stop the motor.
Simulating an Attack on Industrial Control Systems
So far, this setup has the required functional and safety elements, but has no protection against potential cyber threats. This is dependent on how the industrial process is supported by the IT infrastructure (such as a Windows system to program the device, Ethernet technology, etc.). For example, industrial protocols are mostly unencrypted, which could allow several types of attacks against the system. One example would be a replay attack, where a threat actor spoofs a legitimate system to send illegitimate commands.
We simulated a replay attack on the ICS process by targeting the servo motor system that is being used to rotate the table, and forcing it out of sync with the PLC. The switch has security precautions that limit which MAC addresses can send data, but we can spoof a legitimate node (such as the PLC itself) in order to send a flow of packets to our target without restrictions.
The simulated DoS attack is initiated from an external device, such as a laptop, connected to the system with an Ethernet cable. This loss of timely communication forces the system into the fail-safe state, where a hazardous condition is managed by the secondary safety function of the PLC. This process is illustrated in the video below, as the motor abruptly stops during its normal operation. This forces the process to halt, requiring operator attention and intervention.
In this case, a laptop was directly connected to the industrial system. This is not a requirement for a successful DoS attack, since the same flow of packets could be sent from an uplink, or from an operator’s workstation to the same switch. The threat actor could be in any level of the Purdue model connected to the servo system, and multiple avenues could be used to initiate the attack.

Why ICS Security and Network Monitoring Are Key
As seen in the video, we were able to completely halt the motor’s function. However, it could have been easily prevented if cybersecurity best practices were implemented.
The first security item to consider in a real operation is if the network is properly set up. For example:
- Are switches configured properly, using features like safety ports so that unique MAC addresses are bound to specific ports? If ports are restricted, this type of access to industrial systems is blocked.
- Are firewalls used in higher levels of the Purdue model? The port of an industrial protocol should be blocked when used in the wrong VLAN, and communications that pass through to lower levels can be allowlisted.
Another layer of defense is to have an intrusion detection system (IDS) that detects attacks and unusual behavior, allowing defenders to act before process disruption occurs. The best of these systems also identify vulnerabilities and cybersecurity weaknesses, like weak passwords and open ports.
While our demonstration shows how easy it is for an attacker to disrupt production, it is also possible to prevent downtime and ensure functional safety by implementing layered ICS security defenses and network monitoring technology.