A crucial part of threat intelligence is being able to share threat information and indicators of compromise (IOCs). To do so in an effective way, it’s important to have a common structured format, such as STIX. Starting from version 2, the STIX format implements a standard to define and reference kill chains.
This blog covers one way to use this feature with the MITRE ATT&CK framework, a knowledge base of tactics and techniques based on real-world malicious activities. We also show an example usage of STIX based indicators created by Nozomi Networks Labs to show how a standardized format can help threat intelligence sharing.
The ATT&CK Framework Provides Real-World Threat Intelligence
MITRE ATT&CK is commonly used to describe and classify how malicious actors conduct reconnaissance, initial access, persistence, lateral movement, exfiltration, and many other tactics. Malicious events are categorized by one or more specific techniques which are grouped into high-level tactics.Currently, ATT&CK tactics and techniques are divided into Enterprise, Mobile, and Industrial Control Systems (You can learn more about using MITRE ATT&CK in this blog). All the techniques are grouped by tactics and can be identified by their IDs.
MITRE ATT&CK tactics and techniques are increasingly becoming a standard that helps both blue and red teams. From the offensive point of view, the framework creates a precise model of a specific attacker’s behavior and the possibility of emulating it. From a defensive point of view, analysts can use MITRE ATT&CK to structure and share threat information. It is also possible to create analytics to establish trends in malicious actors’ attack techniques.
ATT&CK version 10, just released, includes new data source objects representing various information that can be collected by sensors and logs. Each data component describes specific properties of a data source, allowing detection of a specific Technique. As usual, this release also includes additions and improvements to Techniques, Groups and Software in Enterprise, Mobile and ICS matrices.
The Importance of Standard Formats
Information sharing helps expand everyone’s cyber threat intelligence. The more intel we share, the more we can aggregate insights and can anticipate and respond to attacks faster and more effectively. One important condition for sharing threat intelligence is to rely on standard formats to make contributing and ingesting data easier.
Structured Threat Information eXpression (STIX™) is a language and serialization format used to represent cyber threat information and exchange it consistently and efficiently. As this white paper notes, STIX also provides a way to share a wide set of information including:
- Cyber observables (e.g., a Registry key is created, network traffic occurs to specific IP addresses, email from a specific address is observed, etc.)
- Indicators
- Incidents
- Adversary tactics, techniques, and procedures (TTPs) (including attack patterns, malware, exploits, kill chains, tools, infrastructure, victim targeting, etc.)
- Exploit targets (e.g., vulnerabilities and weaknesses)
- Courses of action (e.g., incident response or vulnerability/weakness remedies)
- Cyber attack campaigns
- Cyber threat actors
MITRE ATT&CK Tactics and Techniques represent adversary behaviors at different levels of abstraction. As we mentioned earlier, STIX indicators are commonly used to represent exactly this sort of information in a structured manner, as such an ATT&CK can easily be expressed within STIX.
Differences between STIX 1 and STIX 2
In the first version of STIX, indicators were expressed using XML syntax. One of the biggest changes between version 1 and version 2 is the transition from the XML to the JSON format, which allows for a more lightweight syntax which is easier to parse and therefore preferred for development.
Version 2 comes with two validator tools: STIX validator verifies if the JSON content conforms to the specification, while Pattern validator tool checks that the pattern syntax is correct.
Another interesting new feature is the STIX visualization: since a large JSON might not be easy to read, the visualization tool is provided to visually show the JSON file as a graph with nodes and edges representing respectively STIX Domain Objects and STIX Relationship Objects.
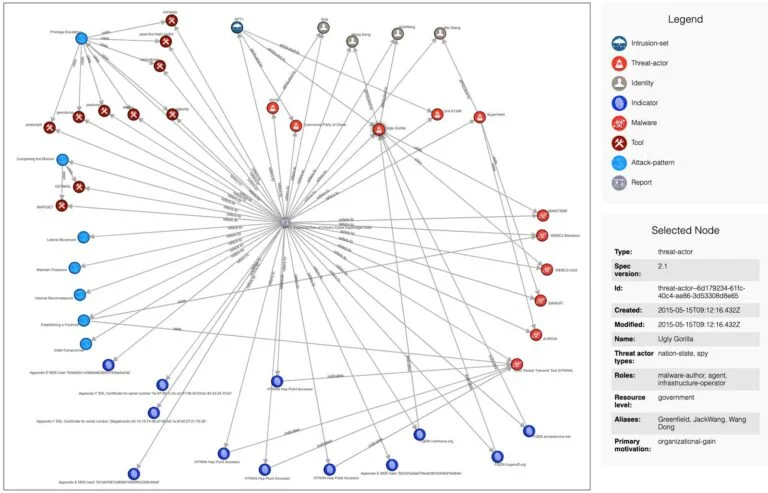
The image below (created using this tool) shows the graph of APT1 based on the STIX v2.1 here. It shows indicators, tools, attack pattern and other valuable information about APT1, a sophisticated threat actor possibly sponsored by the Chinese government (read more details in Mandiant’s APT1 Report).
MITRE ATT&CK as Part of Nozomi Networks Threat Intelligence
Before showing an example of how to use STIX indicators when responding to a ransomware attack, let’s briefly look at how they’re supported by Nozomi Networks.
STIX indicators are part of our Threat Intelligence service, together with Packet Rules, YARA Rules and the Vulnerability database. Threat Intelligence delivers ongoing OT (Operational Technology) and IoT threat and vulnerability intelligence, which is correlated with broader environmental behavior to deliver vast security and operational insight.
Nozomi Networks Guardian currently supports importing both the STIX 1 and STIX 2 formats. Additionally, STIX 2 indicators can be decorated with the applicable MITRE ATT&CK Tactics and Techniques coming from both the Enterprise and ICS matrices.

The following screenshot shows the MITRE ATT&CK techniques detection view inside Nozomi Networks Vantage. This example shows a Lab-created simulation of a real-world attack targeting industrial control systems. As shown in the section dedicated to the MITRE ATT&CK techniques for ICS, this malware gains initial access by replicating through removable media and then exploits remote services to perform lateral movement, with the goal of reaching the engineering workstation (EWS). Once on the EWS, its final target is to change the logic of the PLC which will in turn cause damage to the managed equipment.

Creating STIX from IOCs
Detailed usage instructions on how to create STIX from indicators are provided by Nozomi Networks Labs in the publicly available stix-tools repository. We are going to briefly illustrate an example usage of the tooling in the context of a recent malicious threat.
In September 2021 Iowa based NEW Cooperative Inc. was a victim of the ransomware group BlackMatter (read more details in this blog). It was important for Nozomi Networks to immediately investigate the incident and make sure that their customers were protected against this threat.
During the technical analysis, the Nozomi Networks Labs team was able to extract the malicious domains used as Command and Control during the attack. These indicators and the SHA256 hash of the malicious sample itself were the content of a new STIX file.
All the indicators should be written in the same file on separate lines.

To generate a STIX version 2 file, the script stix_create_v2.py should be used. It is possible to specify MITRE Techniques associated with the threat by using the flag -m, as shown in the following command:
$ python3 stix_create_v2.py -i iocs -o blackmatter_iocs.json -t BlackMatter -d “The BlackMatter ransomware encrypts the document files and asks for ransom in exchange for the decryptor tool.” -m T1486 -s “Nozomi Networks” -u https://www.nozominetworks.com/blog/blackmatter-ransomware-technical-analysis-and-tools-from-nozomi-networks-labs/
The script produces the following output.

The graph representation of the indicators is shown in the following image. The STIX graph shows three indicators (two malicious domains and the SHA256 hash of the malicious binary) connected to BlackMatter and using the MITRE Technique T1486 – Data Encrypted for Impact. The image also shows Nozomi Network Labs as creator of the indicators. In the legend section, more information about external references and the threat description can be found.

Takeaways: MITRE ATT&CK Facilitates Sharing Threat Intelligence
One of the key points in this blog post is the importance of sharing threat intelligence. To do so, it is essential to use standardized formats to share information in an efficient, consistent and compatible way. STIX is broadly used by the threat intelligence community to achieve these purposes.
The MITRE ATT&CK framework is fundamental to understanding the context of a threat quickly and efficiently, and it has become a standard in the security community. ATT&CK can also be used to enrich the information shared with STIX, to enhance threat detection and response.










