IEC 61850, the international standard for digital substation architecture, tooling standardization, and protocols at electrical substations, is a big win for standardization and ICS security. It has been adopted worldwide, enabling utilities and operators to efficiently commission, interoperate and maintain new equipment.
However, one of its communication protocols, GOOSE, although effective, has displayed several security issues. While many researchers around the world have put forward proposals to address the problem, IEC has already defined a standard way to tackle such defects. Let’s take a look at how the IEC approach can be used to improve security for power grids and substations across the globe.
IEC 61850-8-1: The Specification of the GOOSE Protocol
This protocol is used to allow an IED in a substation to share status and events over a process bus. The design behind GOOSE is based on a publisher/subscriber pattern, where publishing happens by means of multicasting events over ethernet, which subscribers can receive and process at will.
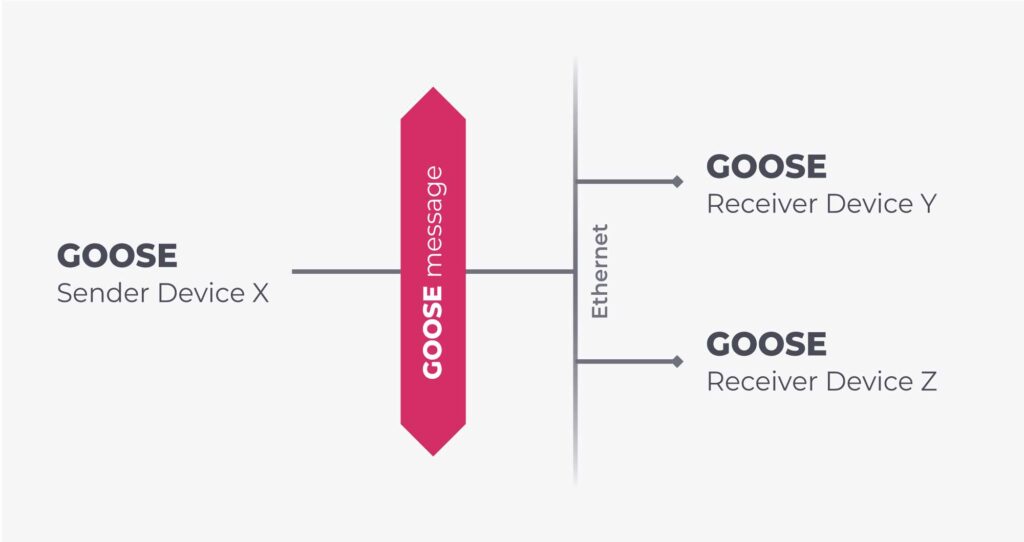
Events are transmitted in conceptual “control blocks” with similar application level semantics. For each GOOSE control block, the protocol adopts two different sequence numbers to make sure that the “newer” status gets used – stNum and stVal. The stNum sequence number is updated when the status changes, while the stVal is updated when the status defined and captured by an stNum value is still valid. The stNum system will continue to grow and evolve (even though there are rules in the state machine for rolling it back to start), while the stVal system will eventually be incremented if the same status remains valid over time.
That being said, since the original protocol is not protected from injection and replay attacks, a malicious actor can threaten substation security by generating a GOOSE frame similar to the ones observed in the network, but with manipulated values. For example, a threat actor can inject a GOOSE control block with a stNum much bigger than the current value to overwrite the real value of the status being sent from the legitimate publisher. There are many variations of the attack, due to the unauthenticated nature of the protocol.
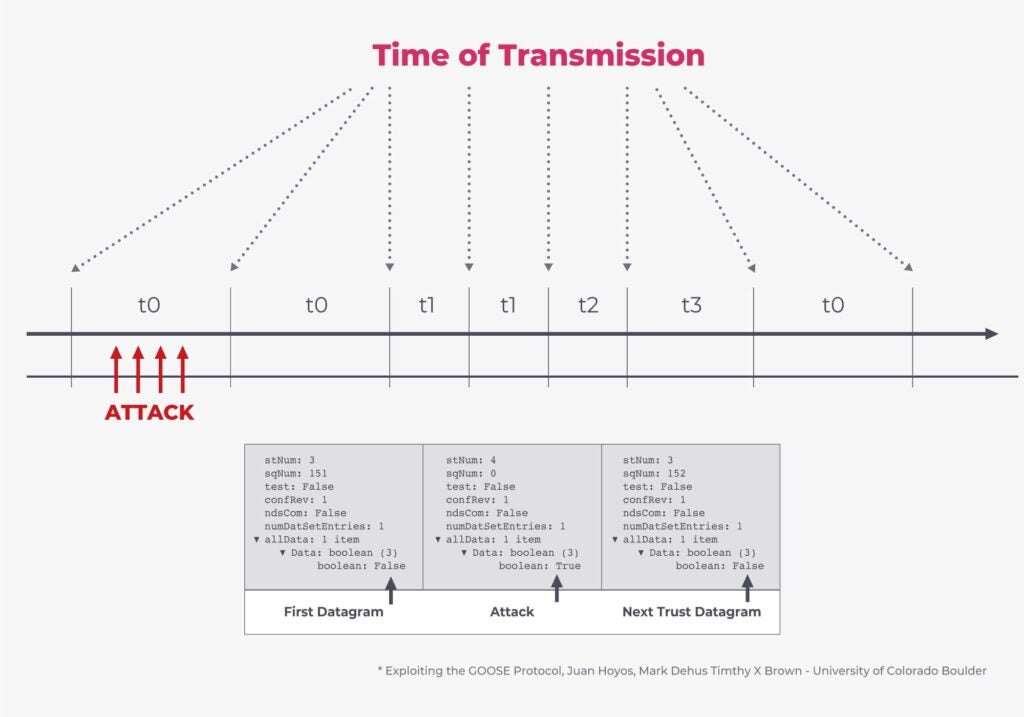
Today, the communication path selection process (i.e. the fact that GOOSE is supposed to be restricted to a logical substation VLAN) is used to restrict the perimeter of devices that send and receive these messages. However, a standardized solution exists to solve these protocol-level weaknesses.
A Solution to the GOOSE Protocol-Level Weakness Problem
Although several different research efforts and proposals have been made, it’s very important to deploy a single standard to guarantee the cross-vendor compatibility that has made IEC 61850 successful.
That single solution is based on the premise that a GOOSE message can now be signed for integrity (and in some cases, encrypted). The key management used for such processes has been standardized as well, to make operations and maintenance easier.
IEC 62351-6 outlines a way to secure IEC 61850 protocols and GOOSE messages by adding a security extension section to the frames.
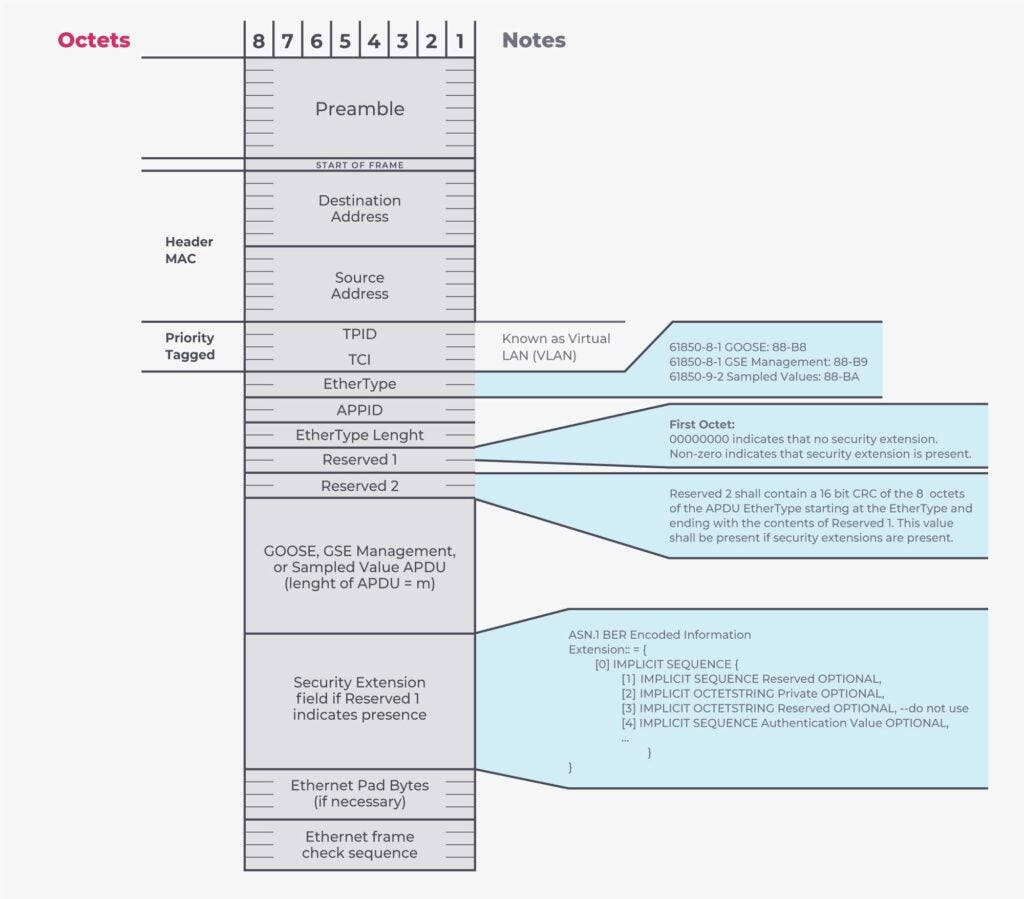
The answer to securing GOOSE protocol-level weaknesses lies in understanding that the Reserved fields (defined in IEC 61850-8-1) can be used to understand whether the Security Extension is present. If so, the Security Extension contains an HMAC of the GOOSE payload, and the necessary information to interpret it.
Of course, generating the HMAC requires having a digital certificate and key management in place. This is where IEC 62351-9 (key management) comes into play. Configuring an IED to properly use security extensions is done using extensions of the SCL (substation configuration language) defined in IEC 62351-6. This aspect is important to guarantee complete coverage of the development life cycle, across protocols and tools.
IEC 62351-9 outlines the key management aspects required by all the protocols and systems defined in the IEC 62351 family of standards. An important role is played by the adoption of the Group Domain of Interpretation (GDOI) defined in RFC 6407. It ensures that GOOSE publishers and subscribers can generate and use valid session keys in an effective and secure manner.
Even though less popular today, IEC 61850-90-2 (Sampled Values) has also been enhanced to include a similar security extension. This approach secures live measurements inside the substation. The same technical considerations and advancements realized for GOOSE are applicable to Sampled Values.
What’s Next: More Enhancements to IEC 62351
The GOOSE protocol has been plagued by vulnerabilities that have finally been addressed in a standardized way, and implemented by vendors. All this being said, more enhancements to the IEC 62351 family of standards are coming to enable a truly secure power grid system. As encrypted communications are adopted, the focus of security monitoring will broaden, from a “check for bad guys” approach to ensuring the health and security of the end-to-end system. For example, making sure that the PKI (public key infrastructure) is not compromised, that certificates are being provisioned and revoked properly, that weak cipher-suites are being disabled, etc.
It will continue to be important for operators to have visibility and security monitoring technology in place. In this regard, the Nozomi Networks solution fully supports IEC 61850 and IEC 62351 and monitors encrypted communications systems for security and validity.










