This article was updated on October 10, 2019.
In the last decade market and cost pressures have driven significant technological advances in automation and industrial connectivity across all aspects of petroleum extraction, pipeline transport and refining. While technological advances are delivering business benefits, systems are now exposed to more cyber risks than ever before.
Yet, according to a 2017 survey by the Ponemon Institute, the deployment of cyber security measures in the oil and gas industry isn’t keeping pace with the growth of digitalization in operations. In fact, just 35% of respondents rate their organization’s OT cyber readiness as high while 61% say their organization’s industrial control systems (ICS) protection and security is not adequate.
One way to overcome the ICS cyber security gap is to utilize next generation technology that leverages machine learning and artificial intelligence (AI) to deal with system complexity and deliver immediate benefits. Let’s take a look at two examples of how a passive ICS anomaly detection and monitoring solution secures pipeline networks.
Improving the Efficiency of New Equipment Commissioning
Quality assurance and quality control (QA/QC) is big business — and a big undertaking for oil and gas operations teams.
Typically, within the command structure between DCS/SCADA, each controller and endpoint must be tested under various process stress-factors and reported in a full-loop test. For example, a test engineer must command a valve to turn a certain percentage under various operational circumstances and record the impact on latency, availability, failure risk etc. This must be done in compliance with various regulations and the results reported.
If a network or device is added into the DCS/SCADA, the process must be repeated. This is arduous and resource-intensive; even more so for remote pipeline networks. However, a passive industrial cyber security and operational visibility solution deployed in the industrial network, as shown in the diagram below, makes these processes more efficient.
How? Let’s first take a step back and explain how the solution is deployed and works:
- Passive ICS cyber security modules are deployed in the industrial network by being attached to mirror or SPAN ports of networking equipment at key segment points.
- The modules copy network traffic to themselves for rapid learning and analysis.
- No out-of-network data is added to the ICS network, and production is not impacted. There is no impact on latency, no risk of intrusion and no risk of network downtime.
- The ICS cyber security appliance leverages machine learning and AI techniques to rapidly analyze huge volumes of network communication and process variable data that are extremely difficult to evaluate any other way.
- This “smart” data analysis is used to model the pipeline system, and develop process and security profiles specific to it.
- Once baselines are established, high speed behavioral analytics are used to constantly monitor it.
- The result is the rapid detection of anomalies, including cyberattacks, cyber incidents and critical process variable irregularities.
In the commissioning scenario, new devices added to the network are quickly identified and highlighted in dashboards and reports using a central management console. Device information such as location, protocols, connections, manufacturer and model number is all available from the remote location.
A test engineer can check device performance by running queries and monitoring the values of process variables against established baselines to detect anomalies. This improves operator productivity and shortens the time to deployment of new equipment.
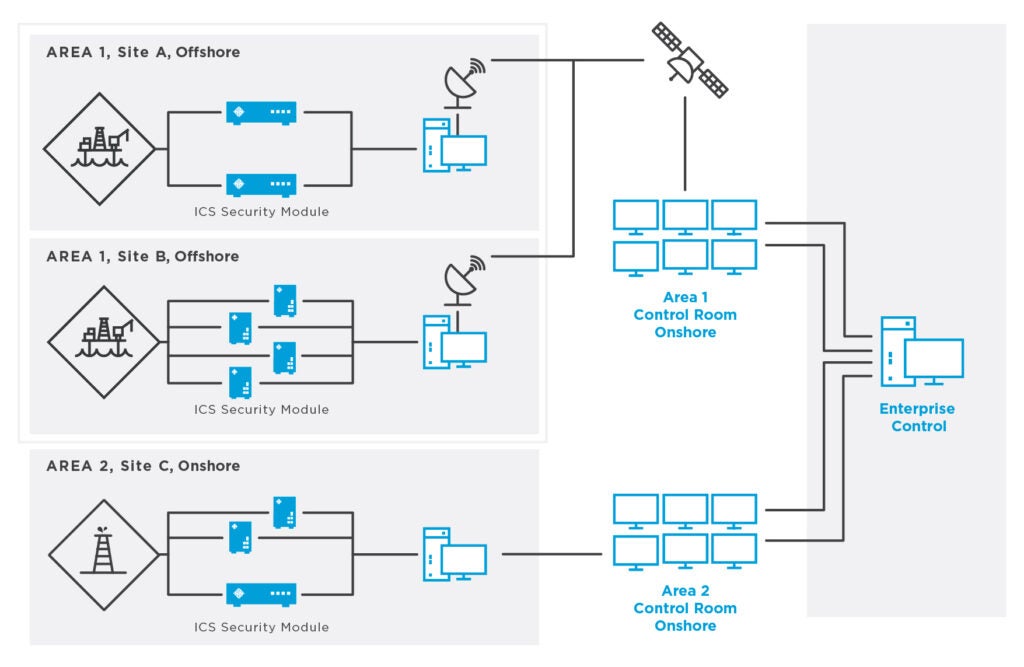
Improving ICS Cyber Security with an Enterprise-Ready Solution
Good ICS cyber security solutions provide operators the ability to monitor networks and security risks across multiple site locations. This is important for achieving robust cyber security monitoring and operational excellence in any large-scale oil and gas control endeavor.
Typically, this is achieved with a multi-tiered ICS cyber security approach whereby geo-distributed networks with passive ICS cyber security appliances are linked together with a centralized console or virtual interface. This allows offsite, centralized, real-time monitoring of cyber threats and risks, anomalous changes to pipeline flow variables and network communication irregularities.
If cyber risks or new nodes are detected, field operations and centralized control can work in concert to identify, evaluate and consistently improve operations and mitigate risk. This is directly applicable to pipeline networks where small changes in traffic flows or device behavior could indicate a cyber threat or potential point of failure.
An enterprise-ready passive ICS cyber security solution allows OT and IT users alike to clone useful dashboards and network queries for use on new appliances. Items like table views, compliance metrics and report templates are quickly duplicated and achieve a unified approach to ICS security and operational management. Device and network traffic can easily be compared from site to site, significantly reducing mitigation, troubleshooting and forensic efforts.
Address the ICS Cyber Security Gap with Passive Anomaly Detection
To deal with the challenges of increasing digitization and cyber risks, oil and gas operators need to be aware of how new technology solutions can help. Passive ICS anomaly detection tools, such as our Guardian and Central Management Console (CMC) solution, utilize machine learning and AI to quickly learn complex pipeline systems and monitor them in real-time.
This solution is non-intrusive, simply to deploy, and immediately starts providing useful, actionable information that reduces cyber risks and improves operational efficiency. Furthermore, with flexible data aggregation available via the enterprise-ready CMC, real-time cyber security and operational visibility is available across decentralized and geographically dispersed operations.
To find out more about the current state of ICS cyber security, don’t miss the SANS report available below.









