A small 20-person rock crushing operation recently suffered a cyberattack that shut operations down for the day. One of the company’s conveyor belt control systems was unable to sense if it were on or off, so the belt kept moving. Product continued to roll in, unfortunately resulting in over $100,000 in damages and unplanned shutdown.
Whatever size operation you have, malware and attacks that impact cyber-physical systems can be harmful to both finances and safety, alike.
“As we think about security, regardless of the size of the environment, it usually starts with, ‘Hey, give me something that’s transparent,’” said Rick Peters, Operational Technology Global Enablement Director at Fortinet. “No one’s looking to take on load or latency in their environments. So, they need a security system that runs in parallel, that’s very transparent and provides them with the intelligence and insight they need. They need some level of control so that if something starts to happen, they can contain the problem and keep the environment associated with the primary function clean.”
In the past, physical security and cybersecurity were different domains, addressed by different professionals using very different tools. But as energy, manufacturing and other critical infrastructure sectors move towards digitally connected environments, the security relationship between physical and cyber is tightening. These days physical assets are internet-enabled, requiring OT leaders to lock down all kinds of physical assets, to prevent security entry point breaches.
“You hear the term convergence thrown around an awful lot, or digital transformation which is purposeful change driven by executives seeking operational efficiency. However, there’s a consequence of doing such things. For example, there are vulnerabilities associated with legacy technology. So operational technology (OT) creates its own cyber-physical burden. Today, you need to protect the cyber-physical.”
Protecting a Growing OT / IoT Attack Surface
In the era of the Industrial Internet of Things (IIoT), devices not traditionally connected to the internet are now all plugged in and capable of communicating. This includes CCTV cameras, door locks, and card readers – along with industrial automation and controls systems (IACS) – just to name a few.
“This goes beyond the traditional enterprise of OT,” Peters said. “If you’re focusing on operational technology or critical infrastructure, you’ve been fortunate in that it’s reflective of a well understood infrastructure framework based on the Purdue model. Now, we’ve gone way beyond that, the expanded attack surface is a very legitimate concern. How do you know that the devices with video or audio capabilities that provide access to your business or home, are properly controlled and not being used to someone else’s benefit, like a competitor or hacker?”
One well-known, classic cyber-physical attack involved the 2016 Mirai botnet which took advantage of insecure IoT devices to allow its developers to scan big blocks of the internet for open Telnet ports. They then attempted to log in using common, default username/password combinations for these devices. As a result, the botnet developers were able to compromise a huge collection of closed-circuit TV cameras and routers.
“The Mirai attack is a perfect example of the vulnerabilities of OT and IoT devices. Manufacturing enterprises can be exposed through IoT elements that haven’t been considered security risks before. Manufacturers have to make sure that devices like cameras and locks on doors, all the physical components within the operation that are now connected, are cyber secure as well.”
Rick Peters, Operational Technology Global Enablement Director, Fortinet
Capabilities and Technologies
Security professionals need the capabilities and the technologies to protect and defend the expanding attack surface.
“When we talk about visibility, control and automated awareness, you can extrapolate your thinking about physical assets. Otherwise, it’s the weak link in the chain. You might have invested greatly at the SCADA level or even implemented broad segmentation to accomplish control. But when it comes to the physical plant, you’re going to have holes punched in your security blanket simply because you haven’t paid enough attention to OT and the proliferation of IoT devices,” Peters said.
At the risk of oversimplifying, it’s like making a big investment in securing your front door, and then leaving the windows wide open.
This is where visibility comes into play. It’s critical to integrate a security solution that allows you to actually see what’s happening on the network. Whether it’s an unauthorized person walking in the door, a process anomaly or an attacker trying to infiltrate the network via a physical security device, network visibility is yet another line of strong defense.
“Visibility is not just detection – it’s understanding and characterizing the device,” Peters said. “It is possible to continuously ensure that devices being introduced into my environment can be trusted. They’re characterized in their current state of security readiness, and I treat them as I treat every single element because all elements provide access to what I need to protect.”
Nozomi Networks and Fortinet Unlock Visibility Across OT, IoT and IT
Dynamic environments require solutions that help security teams focus on important incidents, rather than distracting them with every change in the network. Given the explosion in communicating devices, it’s essential to be able to correlate visibility between each component on the network, and identify the “real” anomalies in need of attention.
In February, Nozomi Networks released version 20 to deal with this emerging OT and IoT visibility and security “at scale” dilemma. Our engineering team has created new means to provide visibility and detection for OT networks and beyond. The result was groundbreaking IoT anomaly detection capabilities that identify OT and IoT assets faster, and detect both signature-based and behavior-based anomalies with more precise and accurate alerts.
In addition to highly accurate OT, IoT and IT device behavioral monitoring and anomaly detection, i.e. with minimized false positives and false negatives, v20 provides precise asset identification in dynamic environments, along with persistent asset awareness, even when IP addresses change.
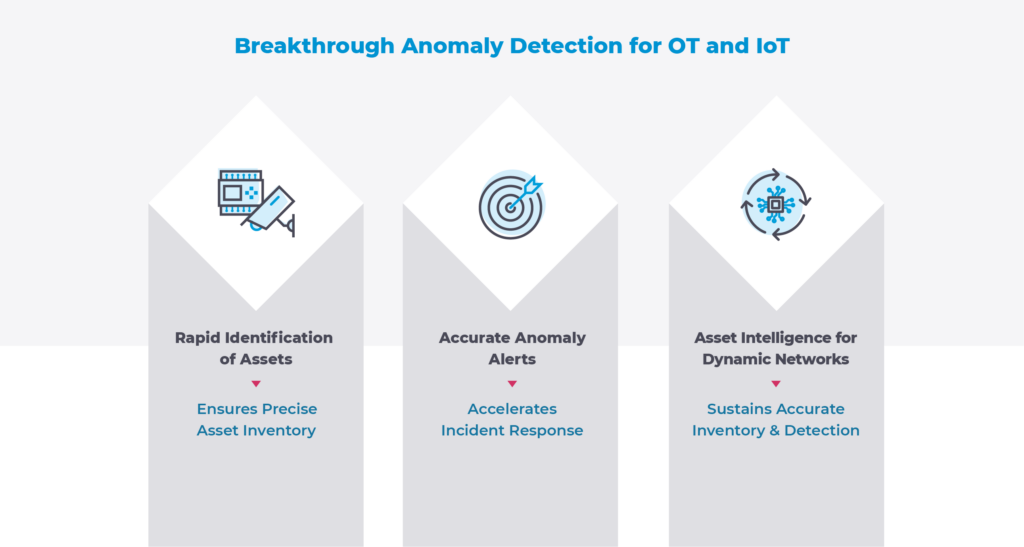
Better together, the combined intelligence with enforcement provided by the integration of Fortinet and Nozomi Networks eliminates blind spots and provides one of the most comprehensive IT/OT network visibility and security solutions available today. Check out my previous blog on Speeding IT Visibility into OT: New Integrations with Fortinet to learn more about the better-together set of integrated solutions from Fortinet and Nozomi Networks.
For more information on v20 and the integrated value offered by Nozomi Networks and Fortinet, please contact us.










