When considering device vulnerabilities, we often think of flaws in the low-level protocols of the software stacks. However, an area of significant risk is the web interface used to manage many of today’s OT and IoT devices.
Recently we analyzed a Power Distribution Unit (PDU), the Schneider Electric/APC AP7920B, in our lab and uncovered a vulnerability in its web interface. We reported it through a responsible disclosure process and CISA and Schneider Electric respectively issued ICS-CERT advisory ICSA-21-348-02 and notification SEVD-2021-348-04, revealing it publicly. This is the latest in a series of Nozomi Networks research findings regarding OT and IoT security.
A PDU is a device that is used to monitor and distribute electric power to the equipment plugged into it. If a threat actor gains privileged access to a PDU, they can shut down outlets and cause equipment reboots, possibly risking operational uptime.
The Schneider Electric/APC PDU in question is a switched rack unit used in physical infrastructure such as energy, transportation and water/wastewater systems. The vulnerability we discovered applied when its management software was used with the latest versions of certain browsers available at the time of research. This means that about ten percent of all desktop browsers worldwide could have been successfully leveraged to execute an attack.1
In this article we describe PDUs, web security fundamentals and the AP7920B vulnerability. This particular problem, alongside other security shortcomings, could allow an attacker to elevate their application privileges from low-level to high-level, providing the permissions and opportunity needed to shut down or cause harm to connected equipment.
Power Distribution Units Protect Critical Equipment
Power Distribution Units (PDUs) are products designed to monitor and distribute electric power to plugged-in appliances. PDUs can trigger alarms for abnormal power conditions and control the distribution of power to specific outlets. They can also be programmed with automatic functions for certain events, such as triggering alarms if abnormal conditions occur, or stopping power to specific outlets. These systems are typically used to control and supply power for critical equipment, efficiently redistributing resources and protecting against potentially harmful line surges.
Like most modern infrastructure devices, the management services exposed by a generic PDU are commonly accessed via a web interface. This interface is accessible from most devices and does not require the installation of vendor-specific software. However, the presence of a web channel also implies that the entire range of web vulnerabilities and attacks that IT administrators have come to know over the years on complex enterprise web applications must be taken into account during the design and development of such a device.
The Schneider Electric/APC AP7920B is a switched rack PDU that fits the description above, allowing remote monitoring and control of connected peripherals through a web interface.
Web Security Fundamentals: Session Management and User Authorization
One of the most important security fundamentals to consider while developing a web application is session management. Session management means tracking a user session on a web service through a stateless protocol such as HTTP. The AP7920B PDU handles a user session through two concurrent secrets:
- A cookie, which is transmitted inside the HTTP cookie header
- E.g.: “Cookie: APCmz1wu40CfLX2LAbp=+01O9I4PeAlqiZgNMutWPcybhEiuV70saqXBX80”
- A token, which is transmitted inside the URL of an HTTP request
- E.g.: “GET /NMC/ovg5z21m+C8sy5fDmHltlA/olstatus.htm”’
These values are randomly chosen by the application. They are set on the user’s browser upon the first interaction with the application, and are renewed at every session-relevant operation, such as after a login, a logout, or in case of a timeout.

The authorization and privileges granted to each user level are another key aspect of web application security. Among the types of users defined in the AP7920B, the device allows the configuration of an “Outlet” user which
“has access to the same menus as a Device User [has read and write access to device-related screens], but with limited capability to change configurations, control devices, delete data, or use file transfer options.”
Notably, the user guide explains that:
“Individual outlets can be assigned to each outlet user. When an outlet user logs into the device, he or she will only be able to view or control outlets that have been assigned to the outlet user.” 2

Vulnerability Description – External Links and Actions Without Anti-CSRF Countermeasures
Outlet users can interact with the Outlet Configuration page for the specific outlets covered by their privileges, as granted by an administrator. Among other things, this page allows the user to configure external HTTP or HTTPS links, which open a new browser window when clicked on.
These external links, according to the AP7920B User Guide, are designed to
“be set to the IP address of the external device plugged into the outlet (if applicable) [or, alternatively,] to the device’s manufacturer web page in order to more easily view user manuals, etc.”

While reviewing the security of this functionality, we noticed an issue with the external links configured by users of the application. The links were neither set with the ‘rel=”noreferrer”’ hardening attribute, nor was a referrer policy defined by the application.
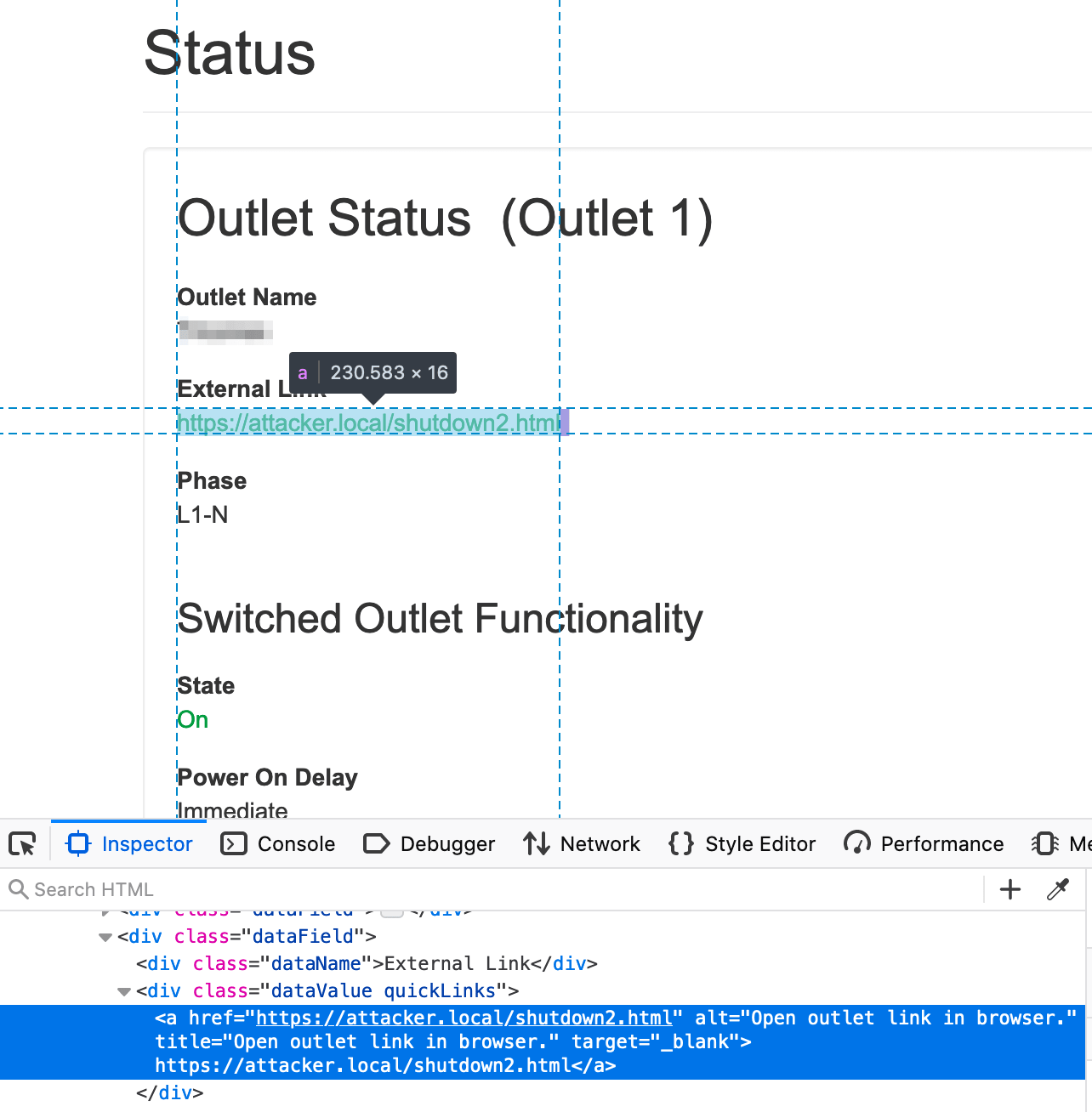

Unless mitigations are specifically applied by the browser (e.g., “strict-origin-when-cross-origin” policy by default instead of the old “no-referrer-when-downgrade” policy3), a security problem can arise. A user could click on a link defined in the application, and the full HTTP Referer header (including the user session token) can potentially be sent to the external domain of the link.4
Furthermore, it was observed that the application does not employ any specific anti-Cross Site Request Forgery (CSRF)5 preventions in security-relevant actions. For instance, the image below shows a cross-origin request for configuring the shutdown of the second outlet:

Notice that no server-side anti-CSRF countermeasures intervened, and that the server replied positively to the request. In fact, the URL token is the only secret that may impede CSRF attacks against the PDU.
The other mitigation which may successfully interfere with an attack is the client-side “SameSite=Lax by default” policy enforced by some browsers (e.g., Chromium-based browsers). This would work since the request is an HTTP POST and the session cookie is set without the SameSite attribute.6
By combining:
- The lack of hardening attributes for external URLs
- The transmission of the token value in the URL
- The absence of other protections against CSRF attacks besides the token
a less-privileged malicious actor can gain higher privileges.
To breach the device, a threat actor simply configures a link to a page, that, if visited by a higher-privileged victim user, can act on the application. For example, send cross-origin GET/POST requests to the AP7920B with the same privileges as the victim. The victim would not know that a successful exploit/attack had even occurred.
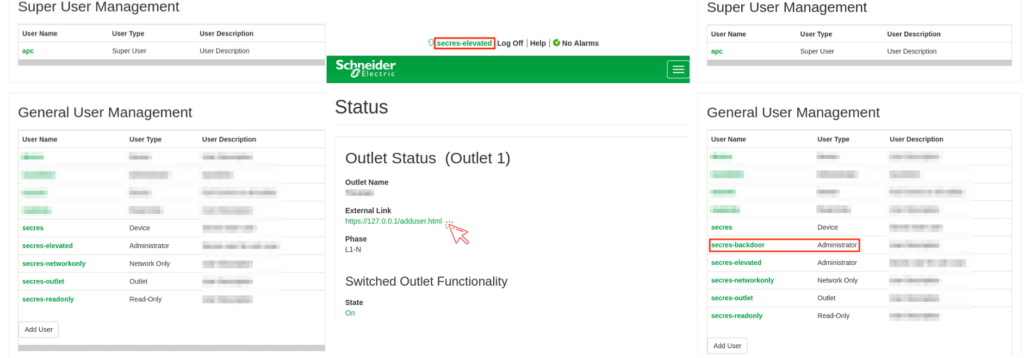
During our tests, an outlet user – configured to interact with Outlet 1 only – was able to shut down a second outlet. This required convincing a higher-privileged victim user to click on the specifically crafted link inserted via the Outlet Configuration page.

Additionally, user creation requests suffered from the same anti-CSRF protection issues as the shutdown request shown above. An outlet user was able to craft a malicious link that created an arbitrary “backdoor” user with administrative privileges in the background. The outlet user achieved full Elevation of Privilege (EoP) if the link was visited by an administrator of the AP7920B.
Web Interface Flaw Threatens Reliability of Cyber-Physical Systems
In terms of browser requirements, the victim must use a browser which simultaneously adopts the “no-referrer-when-downgrade” policy and does not adopt any “SameSite=Lax by default” policy. As of March 2021 (when the vulnerability was discovered), the latest versions of Mozilla Firefox, Microsoft Legacy Edge and Microsoft Internet Explorer satisfied those requirements. This means that about ten percent of all desktop browsers worldwide could have been successfully leveraged to execute an attack.7
Though this issue is subtle, we have just demonstrated how dangerous it can be. To avoid it, we recommend:
- Adding the ‘rel="noreferrer"’ attribute in all HTTP links to external resources of a web application
- Adding a restricting Referrer-Policy HTTP header in server responses (e.g., “same-origin”)
- Or setting a restricting referrer policy by means of a “meta” tag inside HTML pages
Generally speaking, CSRF attacks represent some of the most threatening issues against browser-controllable devices with cyber-physical capabilities. Vendors should strengthen the anti-CSRF protections on the web applications of those devices as much as possible, as even low-risk issues could lead to severe implications.
Schneider Electric released firmware v7.0.6 (for NMC2 cards) and v1.2.0.2 (for NMC3 cards)to remedy the issue. Network defenders should check whether they are using APC AP7920B units, and if present, apply the update or implement compensating controls.
References:
- “Desktop Browser Market Share Worldwide – March 2021,” StatCounter, March 2021.
- “User Guide: Rack Power Distribution Units and In-Line Current Meters,” APC by Schneider Electric, August 2019.
- “Referrer-Policy,” Mozilla.
- “Cross-Domain Referer Leakage,” PortSwigger.
- “Cross Site Request Forgery,” Kirsten, S., OWASP.
- “SameSite Cookies,” Mozilla.
- “Desktop Browser Market Share Worldwide – March 2021,” StatCounter, March 2021.










