A Note to our Customers and Partners in the Middle East
More InformationCVE-2023-45591
A CWE-122 “Heap-based Buffer Overflow” vulnerability in the “logger_generic” function of the “Ax_rtu” binary allows a remote authenticated attacker to trigger a memory corruption in the context of the binary. This may result in a Denial-of-Service (DoS) condition, possibly in the execution of arbitrary code with the same privileges of the process (root), or have other unspecified impacts on the device.
A remote authenticated attacker may induce Denial-of-Service conditions, obtain access to secret information, or, in the worst-case, achieve root Remote Code Execution.
March 4, 2024
This issue affects: AiLux imx6 bundle below version imx6_1.0.7-2.
CVE-2023-45591
CVSS:3.1/AV:N/AC:H/PR:L/UI:N/S:U/C:H/I:H/A:H
7.5
Update to imx6 bundle version imx6_1.0.7-2.
Andrea Palanca of Nozomi Networks
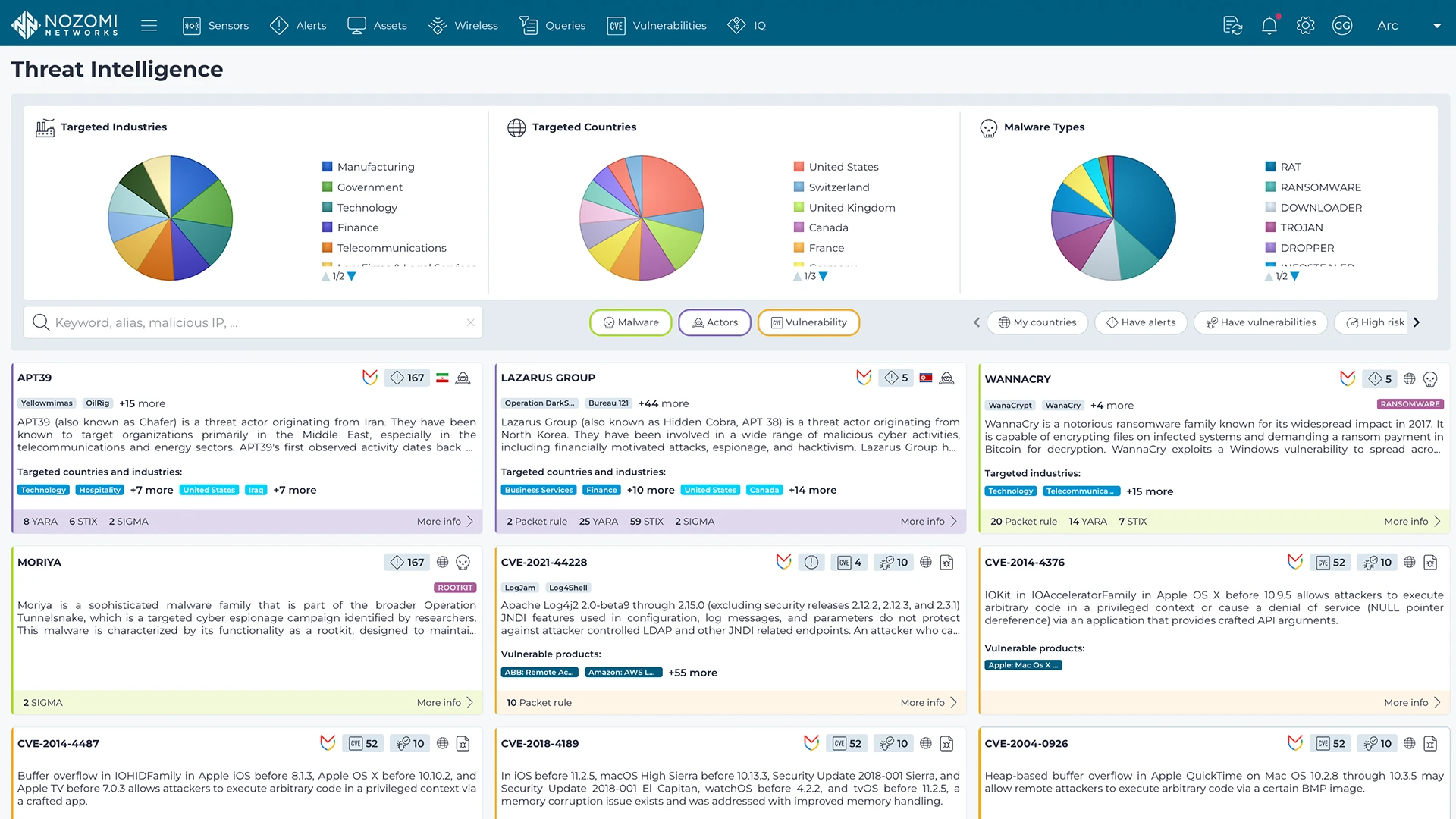
Nozomi Networks Labs curates threat and vulnerability insights that are continuously fed into the Nozomi Networks platform to ensure our sensors can detect existing and emerging threats and vulnerabilities that threaten customers environments.
Learn more