A Note to our Customers and Partners in the Middle East
More InformationCVE-2024-31200
A “CWE-201: Insertion of Sensitive Information Into Sent Data” affecting the administrative account allows an attacker with physical access to the machine to retrieve the password in cleartext when an administrative session is open in the browser.
Clear text password can be retrieved by any user with access to a browser with an active session.
July 7, 2023
Sensor Net Connect V2 (FW version 2.24)
CVE-2024-31200
CVSS:3.1/AV:P/AC:H/PR:N/UI:N/S:U/C:H/I:N/A:N
4.2
No official patch available from vendor. Implement strict access controls for the temperature monitoring infrastructure. This includes preventing regular clients from accessing the web configuration interface, thereby limiting potential points of exploitation. Conduct regular and thorough reviews of logs and user accounts on systems running the Thermoscan IP software. This will help identify and address any suspicious activities early, ensuring that any potential security breaches are caught and remediated swiftly.
Diego Zaffaroni of Nozomi Networks
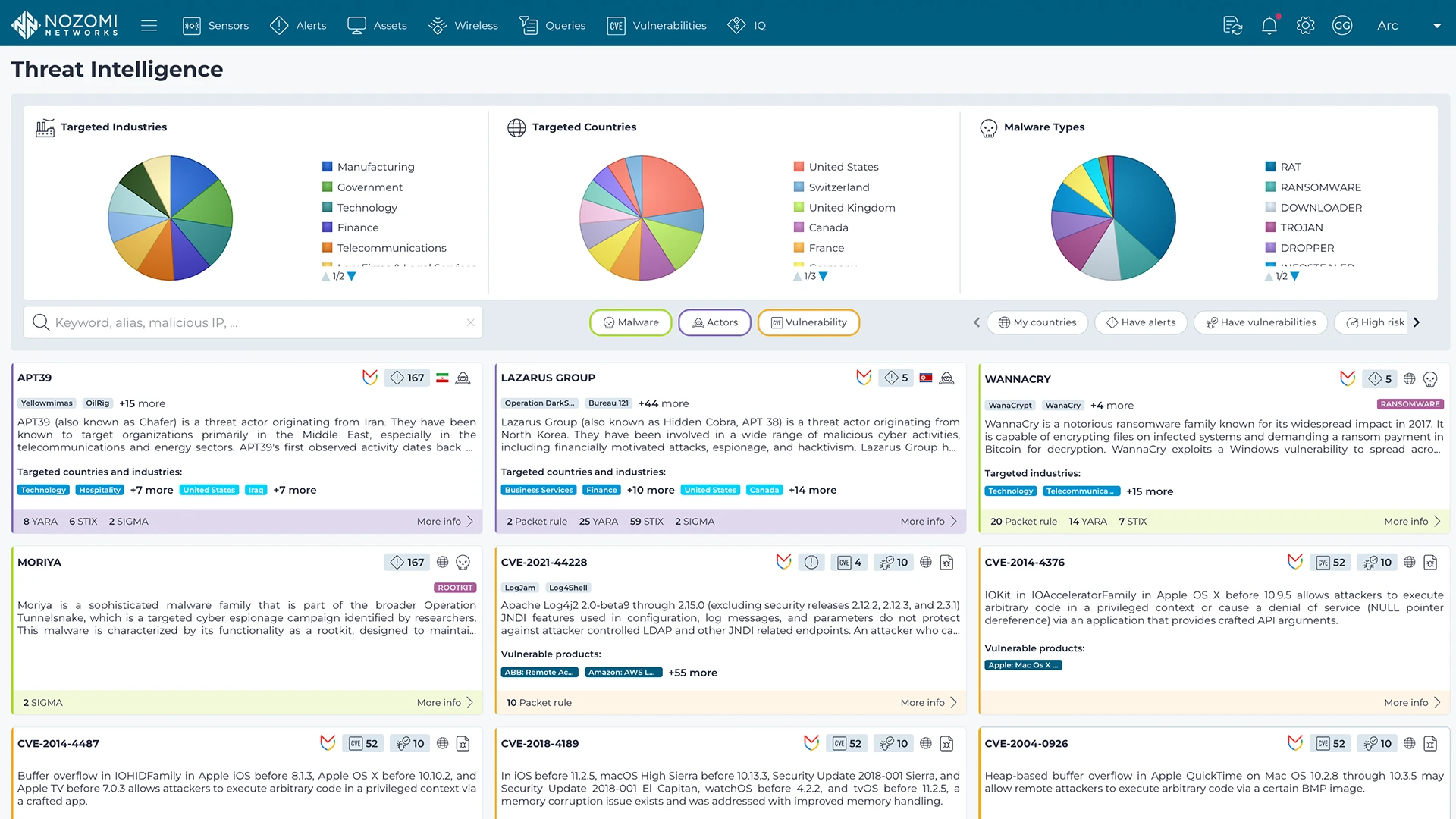
Nozomi Networks Labs curates threat and vulnerability insights that are continuously fed into the Nozomi Networks platform to ensure our sensors can detect existing and emerging threats and vulnerabilities that threaten customers environments.
Learn more