A Note to our Customers and Partners in the Middle East
More InformationCVE-2024-3187
This issue tracks 2 Use After Free (UAFs) vulnerabilities and 1 Double Free vulnerability discovered in Goahead versions <= 6.0.0. These issues are caused by JST values not being nulled when they get freed while performing parsing operation over JST templates. This issue occurs when attempting to process malicious JST server-side templates.
In case the ME_GOAHEAD_JAVASCRIPT compilation flag is enabled and a malicious user is capable of controlling the content of JST templates interpreted at runtime, a remote attacker may attempt to leverage the memory corruptions to either trigger a crash and cause a Denial of Service (DoS) condition over the service or attempt to gain code execution. The latter scenario is extremely context dependent and is not guaranteed to succeed.
October 14, 2024
GoAhead <= 6.0.0
CVE-2024-3187
CVSS:3.1/AV:N/AC:H/PR:L/UI:N/S:U/C:N/I:L/A:H
5.9
It is recommended to apply fixes introduced in version 6.0.1 of GoAhead and use the latest version available as base for building custom web servers.
Diego Zaffaroni of Nozomi Networks
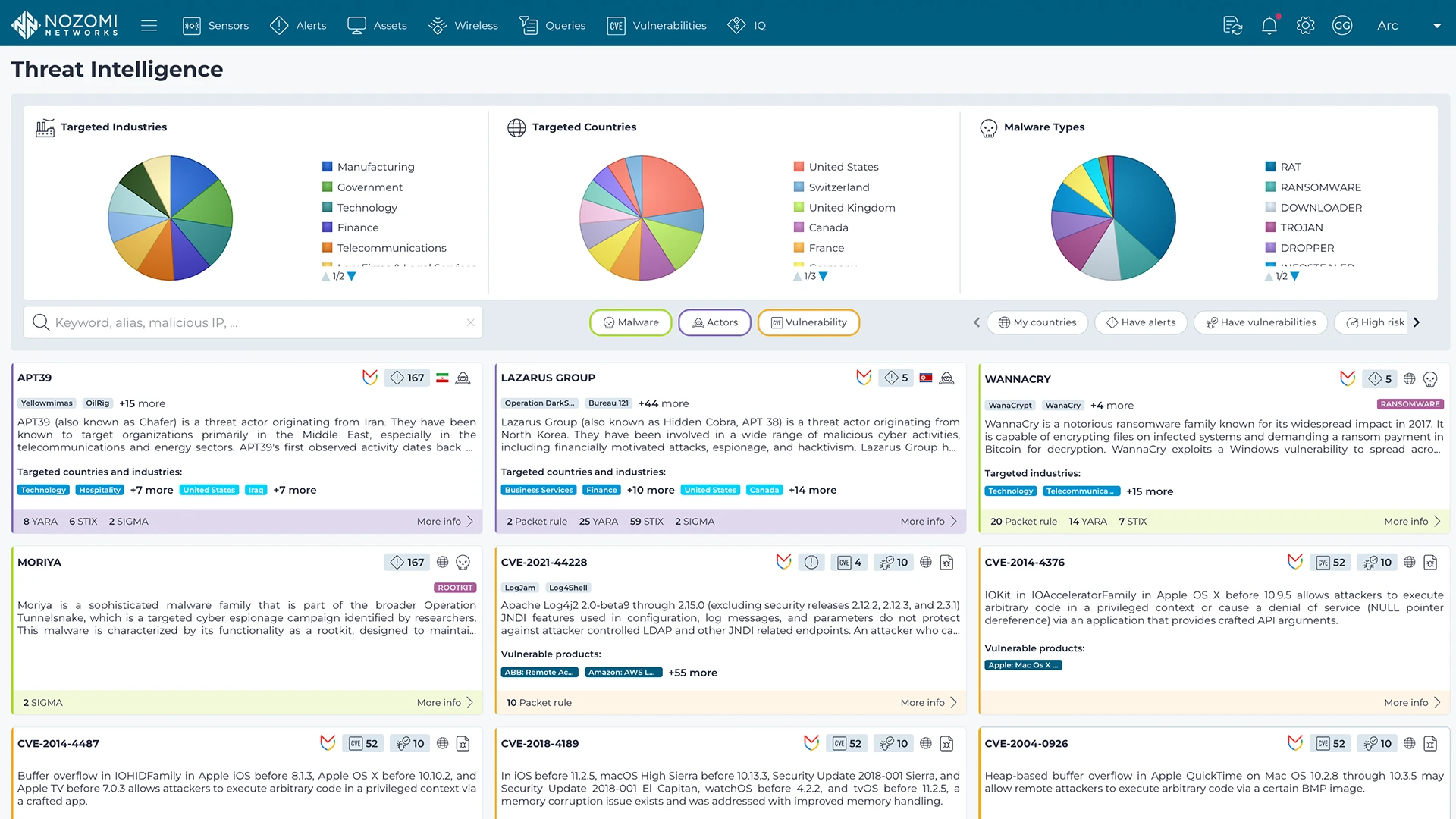
Nozomi Networks Labs curates threat and vulnerability insights that are continuously fed into the Nozomi Networks platform to ensure our sensors can detect existing and emerging threats and vulnerabilities that threaten customers environments.
Learn more