Experience OT & IoT Cybersecurity from the Endpoint to the Air at RSAC 2024
Meet Us at RSA
The TSA Security Directives are issued by the US Department of Homeland Security (DHS). These Directives target critical oil and gas pipelines, rail transit systems and the aviation sector. They require owners and operators to develop and implement a cybersecurity incident response plan, complete a vulnerability assessment to identify potential risks in their systems and report security breaches to CISA within a specific timeframe.
The Nozomi Networks platform provides asset inventory, vulnerability mapping and continuous security monitoring that aligns with the requirements in the TSA Security Directives.
Our solution helps security teams in the oil and gas, aviation and rail sectors implement the requirements in the TSA Security Directives with real time asset intelligence, vulnerability analysis, and continuous security monitoring.
Nozomi Networks’ automated asset identification continuously creates a detailed software and hardware inventory, including open vulnerabilities and system components.
See How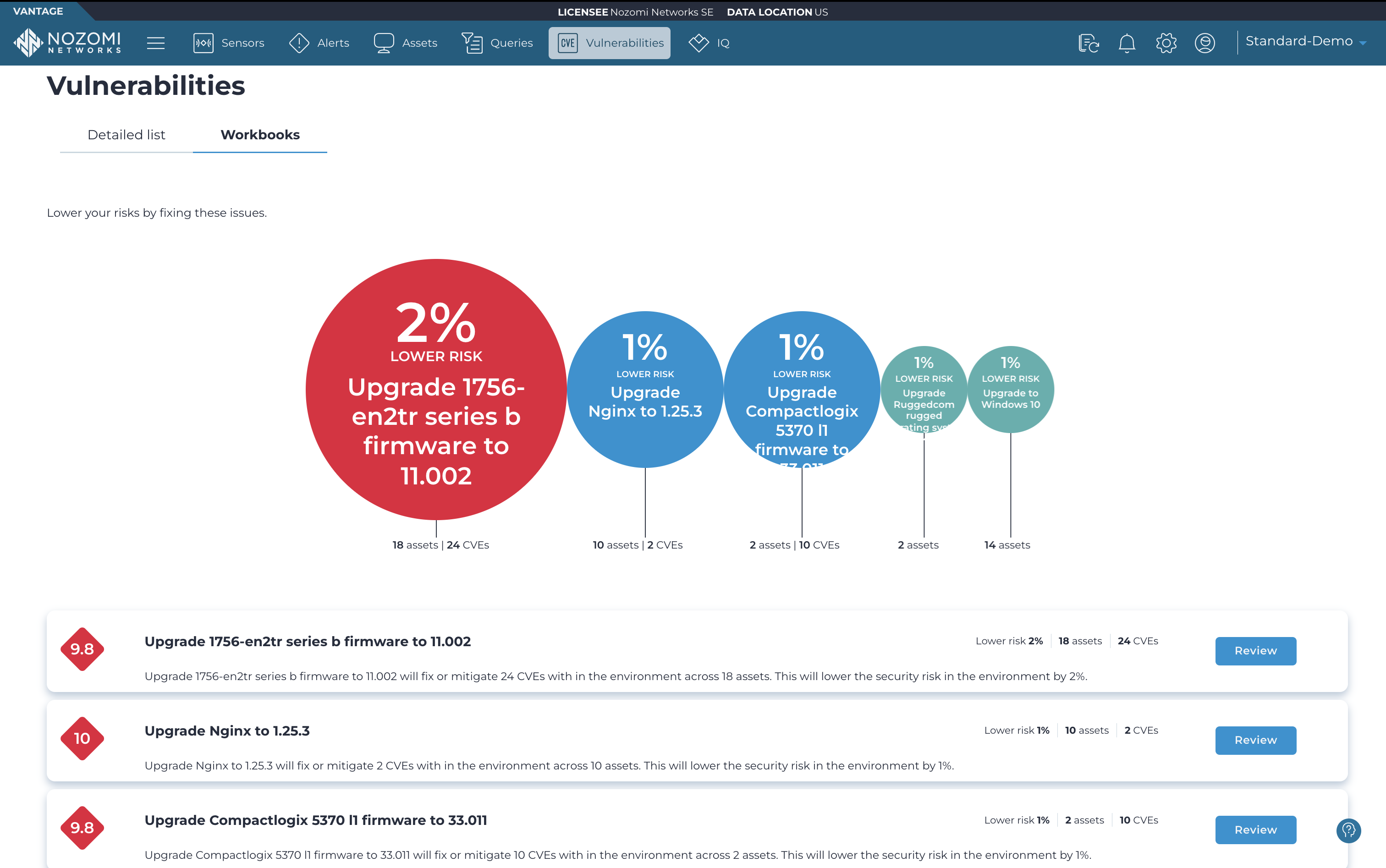
Comprehensive network and endpoint monitoring capabilities provide a real-time view into network segmentation zones, quickly pinpoint anomalies and correlate user activity at the endpoint to proactively prevent impacts from an incident.
View Platform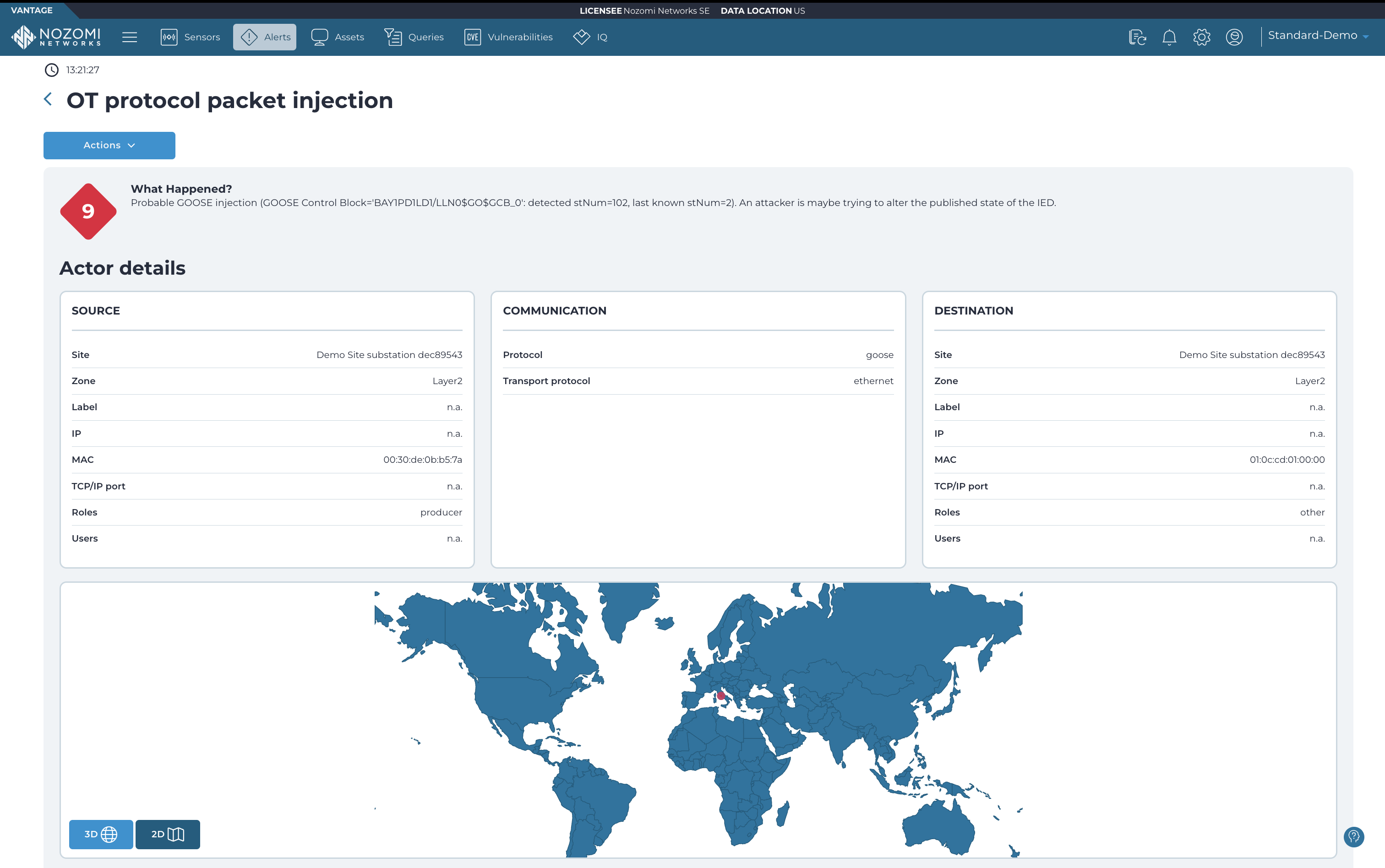
Dashboards, query capabilities, and forensic tools identify root causes and keep you focused on what matters. Detailed security alert and vulnerability mapping provides the information you need to quickly share with CISA.
Learn more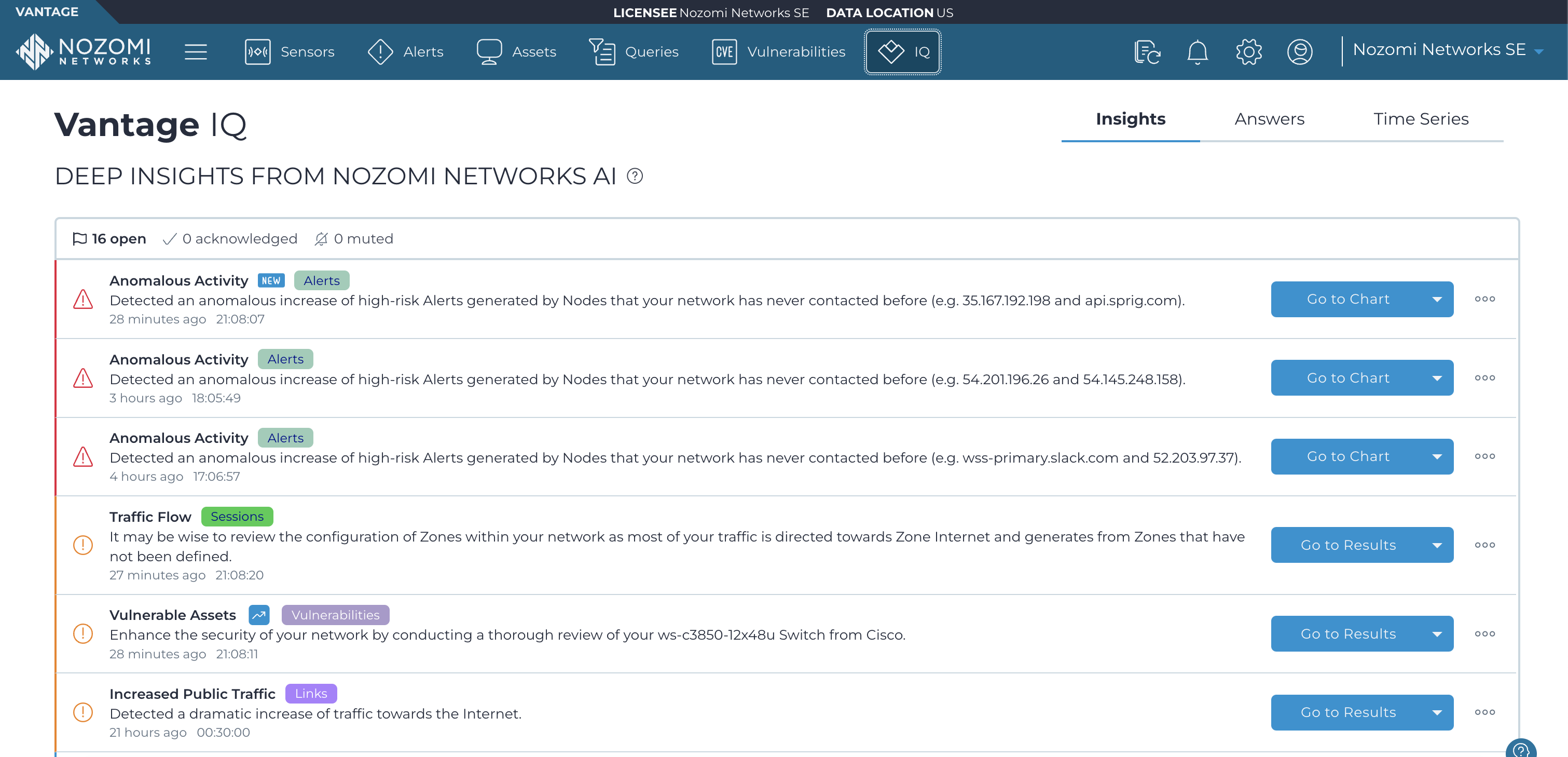
Relationships
We truly value our customers and take pride in having the industry’s highest customer retention rate. But don’t take our word for it. Read why our customers rank us #1 on Gartner Peer Reviews here.
Accuracy & Depth
We are the only vendor with full coverage of OT, IoT, BMS, and Wireless communications, making the flexibility and depth of our asset inventory, vulnerability mapping and anomaly detection capabilities unmatched.
Robust Reporting
Our Dashboards and Content Packs allow users to quickly create a shareable format for the data they need to benchmark their progress and prove compliance.
Sector Expertise
Nozomi Networks is the leader in securing critical infrastructure. Some of the largest oil and gas operators and transportation organizations in the world rely on us to protect their industrial environments.