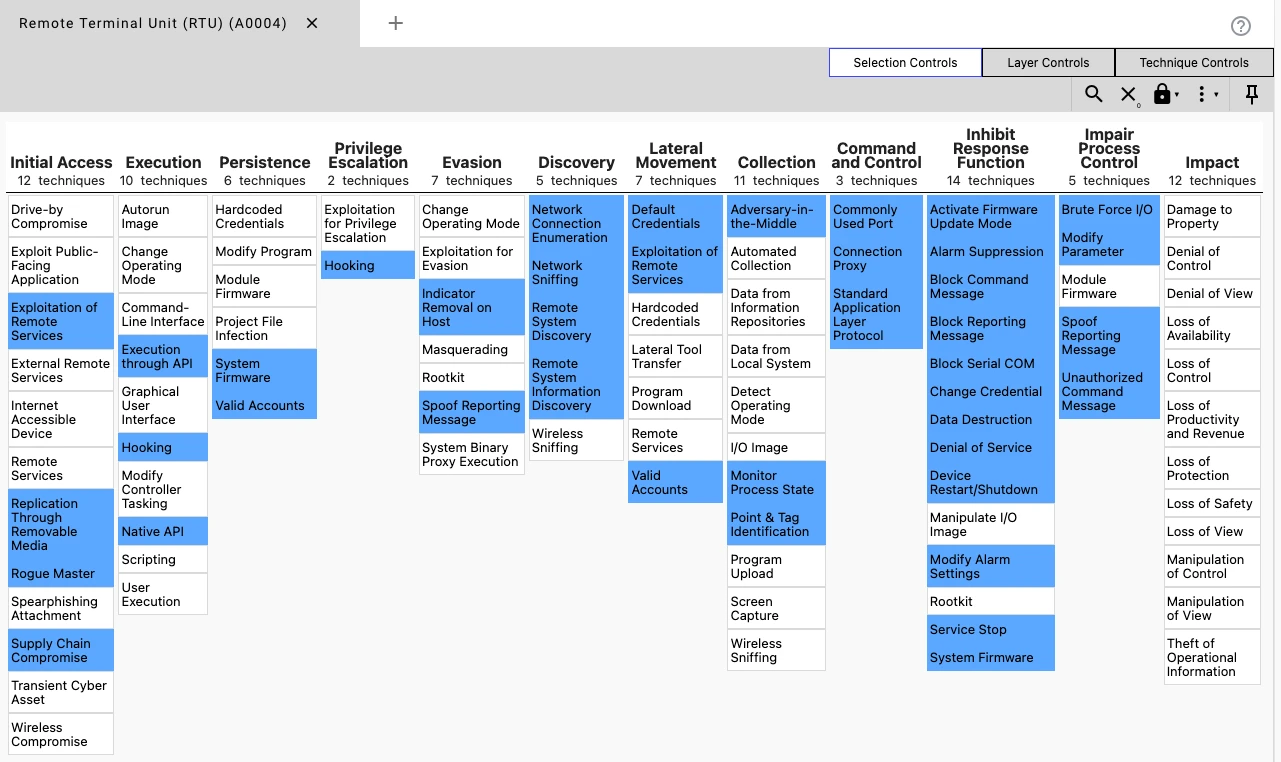
Operational technology (OT) environments are facing a persistent and evolving cyber threat landscape. The MITRE ATT&CK framework for ICS lists roughly 30 techniques relevant to Remote Terminal Units (RTUs), spanning the entire attack lifecycle from initial access to operational impact. The MITRE EMB3D project also highlights methods specifically targeting embedded devices, while our recent Security Report underscores the ongoing and active nature of these threats.
In parallel, industry bodies and regulators are strengthening their focus on embedded device security. This shift is reflected in frameworks, standards, and legislation such as:
- IEC 62443–4–2 – Technical Security Requirements for IACS Components, with its associated ISAsecure Component Security Assurance (CSA) certification, which defines stringent cybersecurity requirements for OT system components.
- Top 20 Secure PLC Coding Practices – industry–recognized guidance for designing, programming, and maintaining embedded logic and configuration securely to reduce vulnerabilities.
- EU Cyber Resilience Act (CRA) – legislation mandating cybersecurity measures across the lifecycle of hardware and software products with digital elements, including OT devices.
Among the most critical OT devices requiring robust protection are remote terminal units (RTUs). These devices collect, process, and transmit operational data from dispersed field locations–such as rural water pumping stations or remote electrical substations–and serve as a vital link between field equipment and central control systems. RTUs enable real–time monitoring and control across sectors including energy, water, and transportation.
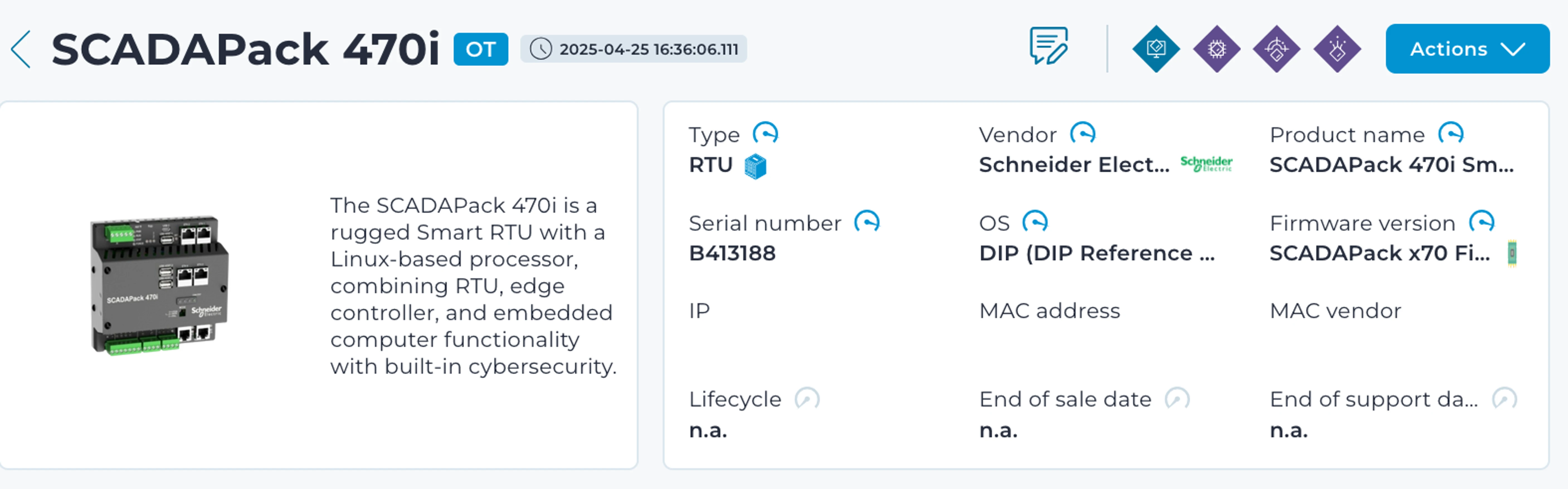
Recognizing that conventional endpoint security cannot be deployed on embedded devices such as RTUs, Nozomi Networks introduced Arc Embedded for embedded devices last year. Now, we are extending its protection to Schneider Electric SCADAPack 47xi Smart RTUs – a cost–effective platform with robust cybersecurity capabilities. This integration brings deep process visibility and real–time threat detection to the control device layer, empowering operators to identify risks early and act without impacting performance.
Key Capabilities of Arc Embedded
Integrating Arc Embedded into Schneider Electric RTUs delivers:
- RTU Asset Status: Full visibility into software and hardware inventory, vulnerabilities, and resource usage–helping teams identify outdated firmware or hardware nearing capacity.
- Level 0 Visibility: Direct access to process variable data from the RTU for insights into physical operations–such as monitoring tank levels or breaker status–without additional polling.
- Threat and Anomaly Detection: Alerts for malicious or suspicious actions, enabling swift investigation and remediation. Detections include:
- Insertion of USB drives – which might be used to introduce unauthorized code.
- Insertion or removal of SD cards – potentially used to exfiltrate sensitive data.
- Use of a mechanical switch to elevate privileges and enable SSH access – a technique observed in the Triton attack.
- Time setting manipulations – which could be exploited to hide malicious activity.
- Changes to control logic – which may alter process behavior.
- Changes to firmware – which could introduce security vulnerabilities.
- Low power supply events – indicating possible sabotage or environmental issues.
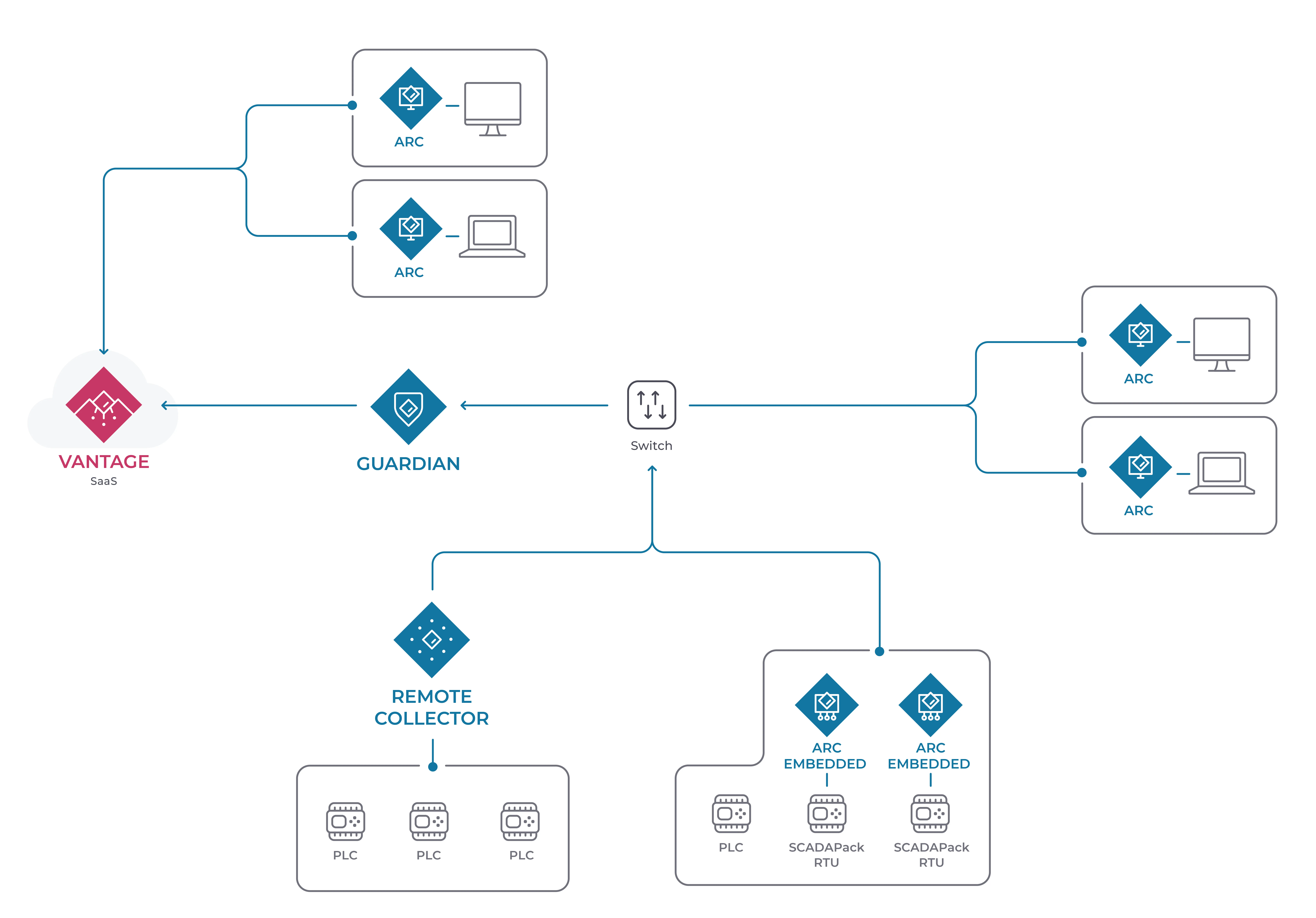
How It Works
Arc Embedded sensors collect asset data and extend asset visibility across OT and IoT networks. Data is seamlessly sent to Guardian or Vantage for analysis and correlation.
Arc Embedded for Schneider RTUs is supported on the SCADAPack 47xi Series. A read/write filesystem overlay on the Edge platform’s SD card is required.
Why It Matters
With Schneider Electric’s global RTU footprint and Nozomi Networks’ expertise in OT/IoT security, this collaboration offers:
- Resilience at the control layer–detect threats before they disrupt processes.
- Embedded protection–no extra hardware, no network slowdowns, no downtime.
- Scalable deployment–rapid visibility across distributed RTUs.











