Released in 2023, Nozomi Arc is a lightweight endpoint sensor purpose-built for OT environments. Unlike traditional EPP and EDR tools, Arc operates primarily in user space, using kernel space modules only when absolutely necessary, mainly in read‑only mode, to ensure precise, controlled interaction with system objects while minimizing write operations and preserving system stability. With the latest release, launched today, it has evolved from the industry’s first endpoint security and network sensor into a full threat prevention solution. As part of the Nozomi Networks platform, Arc is the first OT sensor that is natively integrated with an OT cybersecurity platform and also complements other automated threat response workflows in your security stack.
This breakthrough comes at a time when cyberattacks on critical infrastructure and other industrial environments are increasing and frameworks such as NIS2 and IEC 62443 are demanding proactive defenses.
The Time Is Right for Active Defense for OT Endpoints
Industrial networks are facing a surge in nation‑state campaigns, hacktivist operations and criminal ransomware, all of which increasingly exploit OT endpoints as part of their kill chain. While control devices such as PLCs, RTUs and IEDs remain critical, it is often other OT assets — control servers, operator and engineering workstations, HMIs and historian servers — that act as the real pivot points for attackers. According to MITRE ATT&CK® for ICS, 72% of known ICS techniques directly target these OT assets, and the overlap with MITRE ATT&CK Enterprise techniques makes the exposure even larger. Protecting OT hosts effectively reduces the probability of a successful attack from initial access to lateral movement to impact.
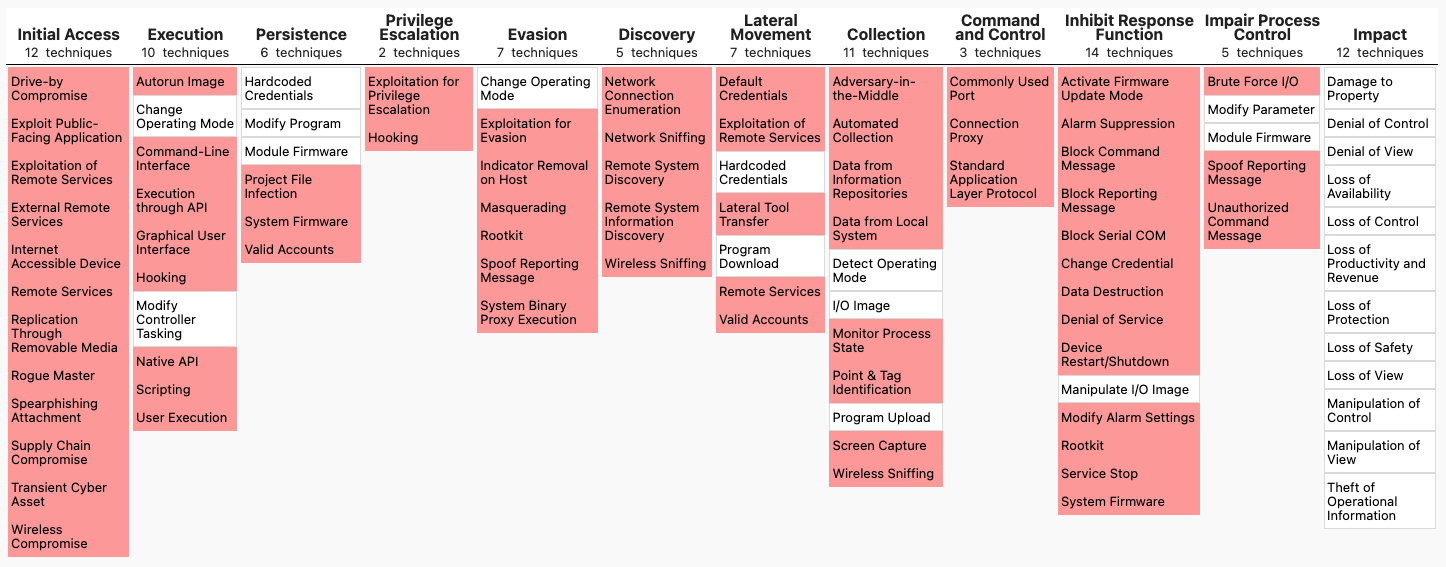
Traditional IT endpoint detection and response tools cannot be applied safely in OT environments: they are too heavy for resource‑constrained systems, often incompatible with legacy operating systems and they introduce unacceptable downtime risks. However, relying solely on passive network monitoring leaves endpoints vulnerable to sophisticated malware and ransomware. Without automated prevention, response remains slow, containment manual and SOC teams burdened with alert fatigue.
Meanwhile, regulatory frameworks such as NIS2 and IEC 62443 explicitly require active defense and malware blocking at the endpoint level. Many industrial organizations cannot yet demonstrate this capability, creating both compliance gaps and elevated risk exposure.
What the industry demands is a lightweight, OT‑safe endpoint prevention capability — one that delivers automated threat blocking and containment without destabilizing operations, and that integrates seamlessly with OT cybersecurity platforms for a unified response. This approach accelerates incident containment and enables enterprise SOC teams to extend detection and response into OT environments.
Nozomi Arc Threat Prevention in Action
The latest version of Nozomi Arc introduces flexible response modes that give asset owners complete control across different environments and risk profiles:
- Detection Mode provides threat awareness for audits and compliance without intervention.
- Quarantine Mode blocks execution of malicious files and contains them safely for forensic analysis and root cause investigations.
- Delete Mode immediately removes malicious files, reducing response time and stopping malicious tools before impact.
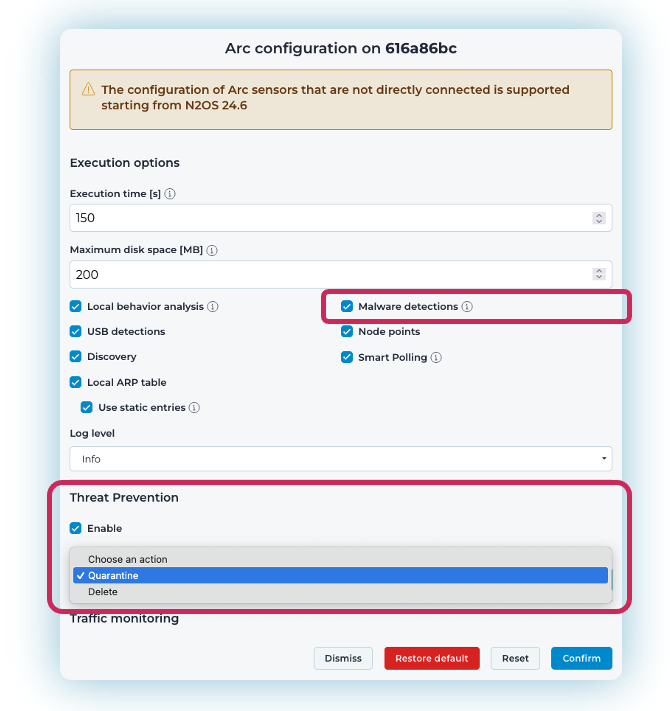
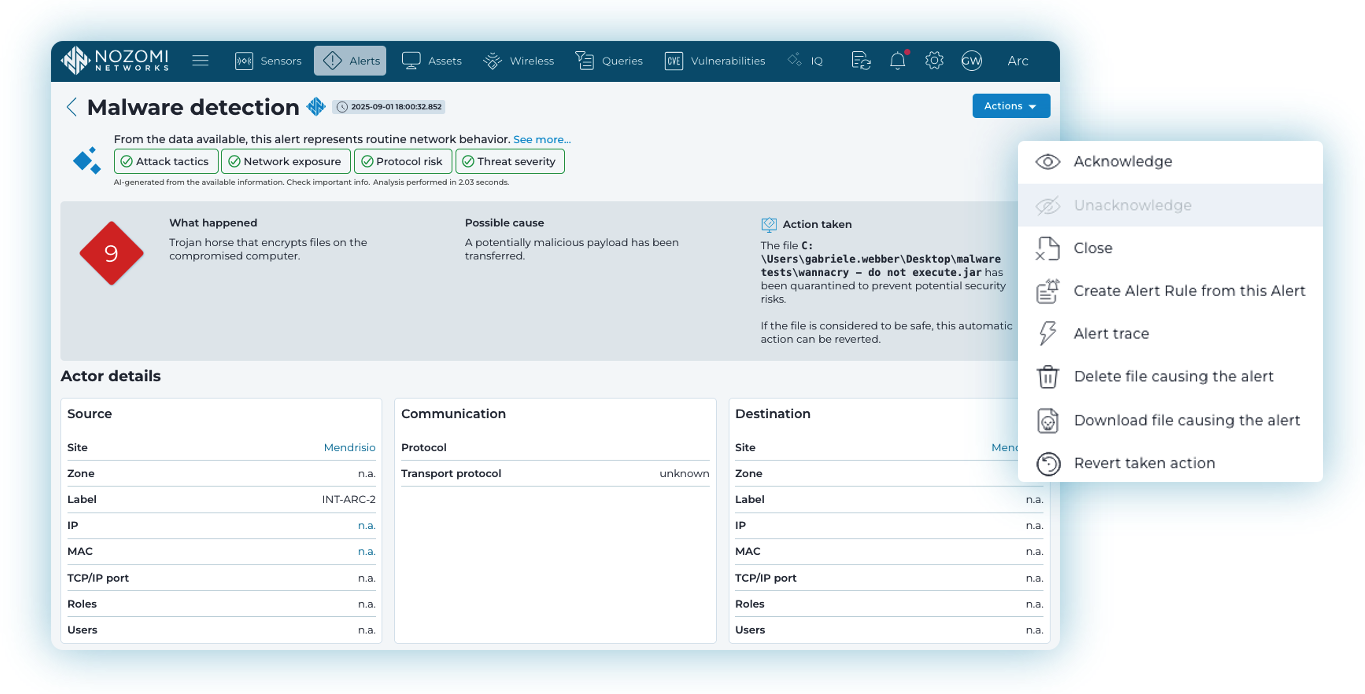
Arc’s detection and prevention capabilities are fueled by Nozomi Networks’ OT‑specific threat intelligence, enriched with the Threat Intelligence Expansion Pack from Mandiant. Together they provide continuously updated indicators of compromise delivered in YARA and STIX formats, along with SIGMA rules for local behavioral analysis.
Why It Matters: Strategic Value for Security and Operations Leaders
ith Nozomi Arc’s ability to safeguard OT endpoints across every stage of a cyberattack — from initial access to lateral movement and final impact — both security and operations teams gain measurable value. For security teams who oversee enterprise‑wide strategy, incident response, risk management and compliance, Arc accelerates mean time to response (MTTR), provides integrated visibility across network and endpoints, strengthens audit readiness, and improves regulatory and insurance posture. For operations teams whose primary goal is continuous and safe production, Arc delivers faster containment that minimizes downtime from intrusions, with the option to choose passive detection only, where practical.
The evolution of Nozomi Arc marks a turning point: industrial organizations can now advance from passive detection to safe, automated endpoint threat prevention, purpose‑built for OT assets. Arc closes the gap left by IT‑centric tools and detection‑only OT security vendors, enabling security and operations leaders to cut cyber risk without compromising operational integrity.
To see the Nozomi Networks platform and Arc in action, request a demo today.












