Critical infrastructure faces the same security threats as other sectors, except that the consequences can be far more serious for millions of people. This is why it’s important that executives in critical infrastructure develop a comprehensive approach to security that encompasses the physical as well as the digital realm—so-called cyber-physical systems.
A unique, global Newsweek VANTAGE survey of 415 executives responsible for security in critical infrastructure shows they are aware of the need for a holistic approach to cyber-physical systems. Nonetheless, they are struggling to overcome cultural resistance to transformational change, especially when it comes to IT and OT systems.
The need to overcome these longstanding obstacles is made all the more urgent by growing cyber threats and the consequences of failing to secure cyber-physical security. Let’s take a closer look at the state of critical infrastructure security in 2020.
Executives Believe Employees are the Greatest Threat to Critical Infrastructure Security
Anybody who is skeptical of the need for secure cyber-physical systems should ponder the results of the confidential survey. Almost all the executives in critical infrastructure say their organization has suffered at least one security incident in the past 12 months and half have experienced two or more. Nearly a quarter say the time between compromise and discovery exceeded 24 hours.
Just as worrying, employees are regarded as the biggest human source of vulnerability—bigger even than cyber-criminal groups. Former employees are also a security risk. The statistics contradict the common view that terrorists and state actors are to blame (they can create havoc, but it’s not common).
How do these attacks occur? More than half are cyber incursions into IT systems, but physical incursions into IT and OT systems are very common too, and this is why it’s important to approach security from both a cyber and a physical perspective. Many say that a lack of integration is the main cause of vulnerability.
These numbers highlight a conundrum: the more integrated are IT-OT-physical systems, the greater the degree of security, but because they are so integrated, these systems are more vulnerable to attack. Clearly executives have to balance the need for efficiency with the imperative for security.
The Consequences of Integrating for Improved Performance, THEN Addressing Holistic Security
Too many organizations are under the impression that their approach to cyber-physical security is adequate, until they find that it isn’t. Complacency can have disastrous results: more than a third of executives say that an actual cyber breach caused them to develop a holistic approach to their organization’s cyber/physical security.
In response to cyber-physical threats, two thirds have integrated some of their IT, OT and physical systems, and the process is continuing. A fifth have integrated all their systems. But here’s the thing, executives see the main advantages of integration as more responsiveness and better decision-making. The fewest number say integration was motivated by the need for stronger security. But experts say a holistic approach to cyber-physical security should precede steps to improve operational performance.
The Biggest Barriers to Better Cyber-Physical Security
In a way, the least surprising result of the survey is what executives regard as the main obstacle to integration. People in IT and OT do not work well together, despite many years of discussion. The survey shows that the main internal obstacles to a holistic approach, both organizational and technical, are big differences between IT and OT in such areas as risk tolerances and operating environments.
Nearly a third says the chief obstacle is cultural – i.e., resistance to change. If there was less resistance, IT and OT personnel would have settled their differences by now. Organizations need to change the culture so that the people in IT, OT and physical security work together to mitigate threats.
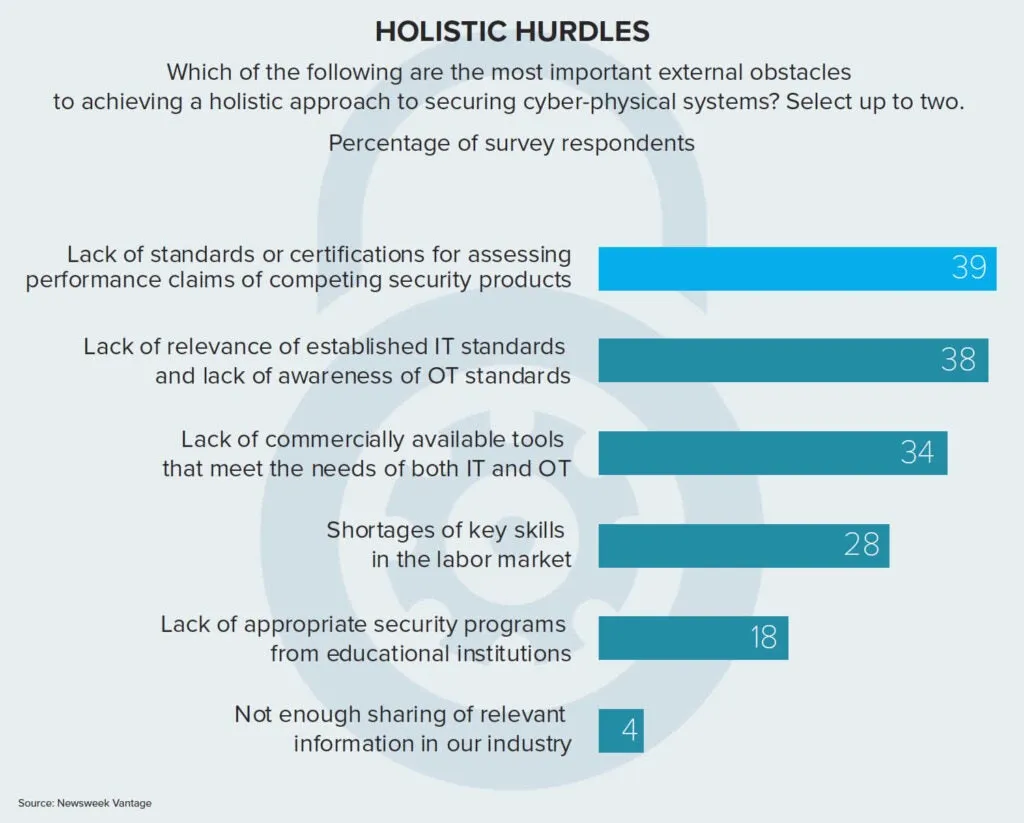
The main external obstacle to a holistic approach is that industry standards for security systems are not used widely enough, even though they are available.
Since the source of friction is largely an issue involving people and their attitudes to work and their colleagues, it is logical that executives say the way to solve this is a more harmonious approach to cyber-physical security systems among the people working in critical infrastructure. Nearly half the executives surveyed say that the best way to overcome obstacles is a detailed action plan of integration supported by IT/OT/physical security teams. To change the culture, they say that security teams must include IT/OT/physical personnel.
Critical Infrastructure Cybersecurity and Physical Safety Go Together
Critical infrastructure organizations are focused on the physical safety of their employees, customers and the general public. If this is jeopardized, they marshal their resources to fight the threat. These organizations need to take the same approach to cybersecurity, especially since a cyber-physical breach could affect public health and safety.
This piece of common sense is, sadly, not common in critical infrastructure. To change the culture, consider four points:
- Cyber-physical standards need to be applied and, where possible, raised.
- Do things in the right order. Design policies and procedures around cyber-physical security and then invest in technology.
- Don’t punish people if they admit to having made a mistake. A security failure is an opportunity to learn how to do things better.
- Cyber-physical security is not like going on a diet. It’s a long-term change of lifestyle.
I urge you to download the full report and see how your organization’s security posture compares to global industry leaders. And, learn from them. Be wise and act BEFORE a catastrophe spurs you to adopt a holistic security approach.









