While the general public might picture drones being used as toys or tools used by film producers, advances in affordable geospatial, data collection and diagnostics technologies have only increased their popularity. Today, we see drones in many industries and use cases like manufacturing, agriculture and surveillance. Taking into consideration that modern drones are able to function at ranges exceeding 10km and with ceilings exceeding 5km, operators can be many miles away from their device while it is conducting missions.
Drones may be deployed for visual inspection of remote or dangerous environments using high-definition cameras, or in conjunction with technologies such as thermal vision. Others may be combined with high accuracy positioning and location for situations such as surveying, condition monitoring and inspection, surveillance and search and rescue. In such critical applications, all parties involved have vested interests in operations being safe, secure and managing risk as much as possible.
As introduced in the first part of the series, Nozomi Networks Labs conducted a security analysis of the Wi-Fi-based QuickTransfer Mode protocol utilized in DJI Mavic 3 Series drones. This protocol facilitates the fast retrieval of images and videos to users’ mobile devices. The primary aim of the research was to reveal potential vulnerabilities that could pose a threat to the drone or lead to data exfiltration. The investigation identified a total of nine vulnerabilities requiring user interaction (QuickTransfer Mode activation).
While Part 1 explained the process of obtaining the firmware from the drone and unpacking it, this blog describes our analysis of the firmware along with the criticality and potential impacts of each vulnerability. These vulnerabilities have the potential to facilitate unauthorized exfiltration of videos and pictures by exploiting the QuickTransfer Mode Wi-Fi protocol.
DJI examined the reported vulnerabilities and identified affected drone models. They have addressed seven of the nine issues, deeming the remaining two unnecessary to fix. As a result, two CVEs were issued with a status of 'disputed'. DJI issued a firmware update to resolve the identified issue for every impacted drone model:
- Mavic 3 Pro: v01.01.0300
- Mavic 3: v01.00.1200
- Mavic 3 classic v01.00.0500
- Mavic 3 Enterprise v07.01.10.03
- Matrice 300 v57.00.01.00
- Matrice M30 V07.01.0022
- Mini 3 Pro v01.00.0620
Services Analysis and Emulation
After acquiring and unpacking the firmware, our first step was to analyze init scripts (including init.rc and all imported configuration scripts) to identify services running on the drone, constituting a potential attack surface. Of particular interest were those services that expose functionalities externally (socket connections, file uploads, HTTP APIs, etc.), as they present an exploitable attack surface for an adjacent attacker (e.g., a malicious application on the mobile device utilizing QuickTransfer Mode). Subsequently, two types of analyses were undertaken:
- Static analysis: the reverse engineering of binaries
- Dynamic analysis: debugging services at run-time
Given that the Mavic 3 firmware is a customized Android build, dynamic analysis was facilitated by executing the target binaries within a fine-tuned Android emulator. This approach enabled the tracing and analysis of noteworthy services using tools such as strace and gdb.
The Wi-Fi Connection
The QuickTransfer Mode protocol creates a Wi-Fi connection between the drone and the mobile device. To initiate the Wi-Fi session, the drone offers a WPA2-based access point when not flying, which the mobile device accesses through the DJI Fly application. This represents a standard communication system on all DJI drones. Figure 1 shows an example of the detected Access Point for a DJI Mini 3 Pro.
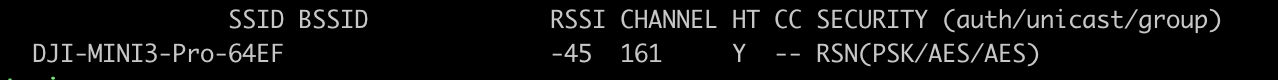
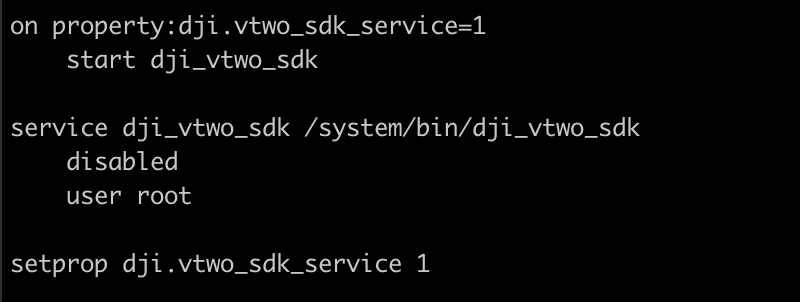
The connection password is generated by the drone and securely exchanged with the mobile device via Bluetooth. Upon analyzing the drone's firmware initialization scripts, it becomes evident that the service responsible for managing the WiFi connection is executed from the binary file located at /system/bin/dji_network, and it is initiated during the boot process (Figure 2).
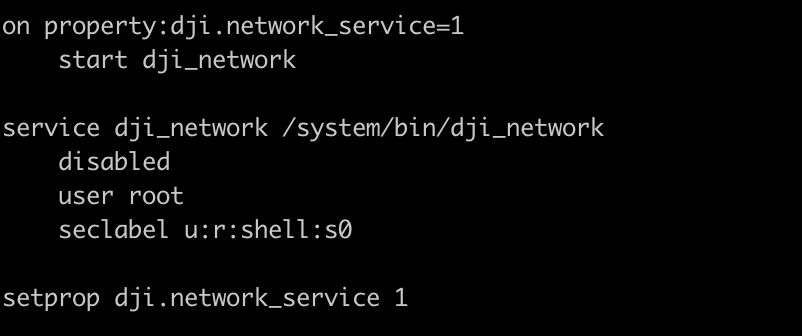
Upon delving into the binary, it is possible to discern that the Wi-Fi password is randomly generated during the drone's initial boot and remains unchanged thereafter. This process is facilitated by the function generate_default_passwd(), which invokes the libc random() procedure four times, as illustrated in Figure 3.
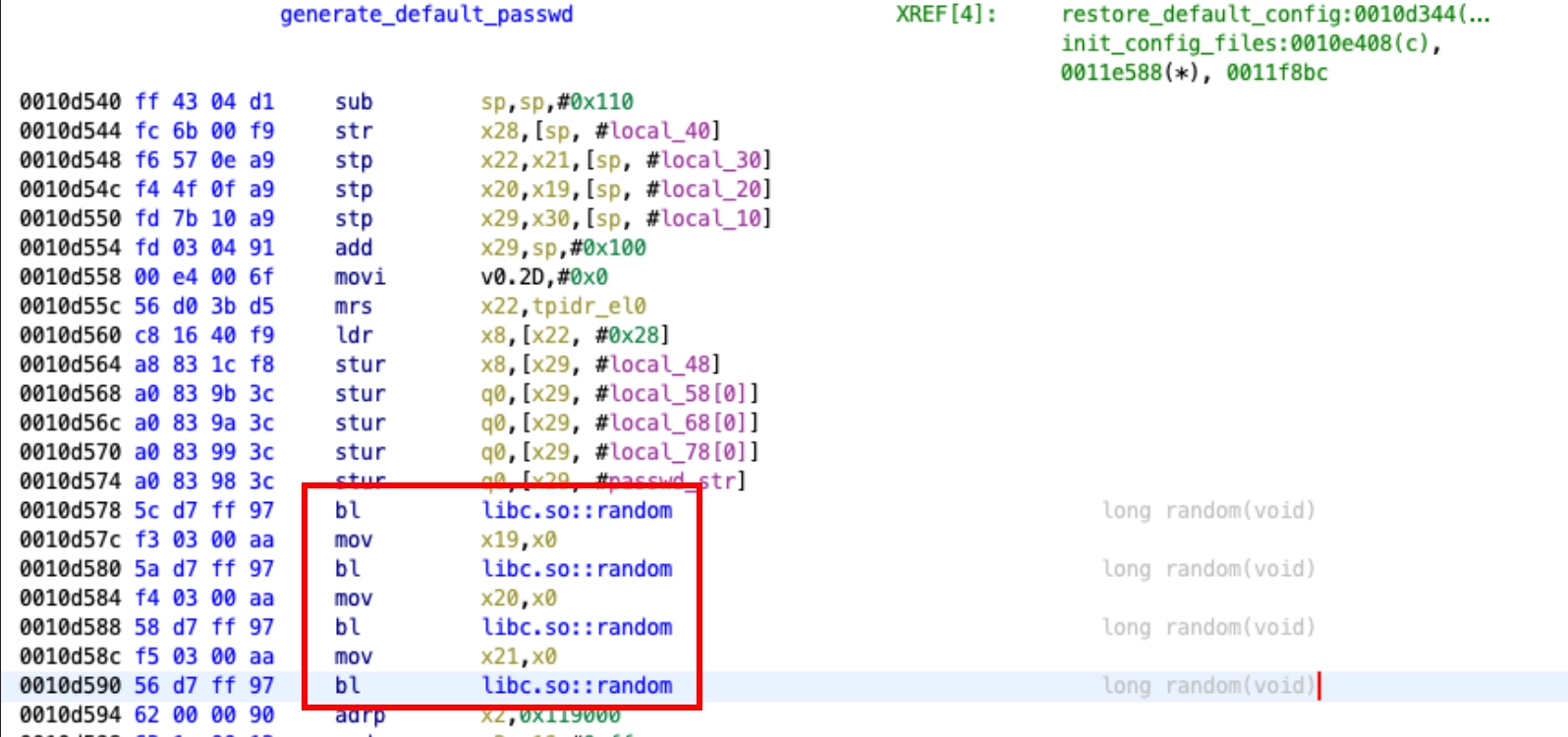
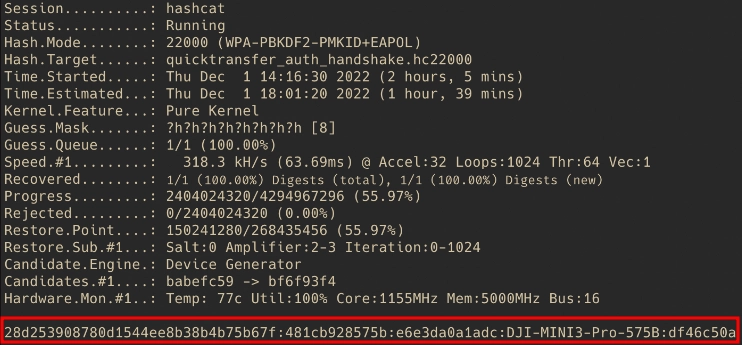
Figure 3 reveals the first vulnerability, since the password is generated as an 8 character string using the hexadecimal charset ([0-9a-f]). With an 8-character password and the 16 characters of the hexadecimal charset, there are only a little more than four billion possible password combinations which, for today’s standards, is not enough variations to be considered secure. In fact, this number of password combinations can easily be cracked with the help of Hashcat tool, or something similar, and a GPU. A quick experiment with a single Nvidia T4 GPU showed that the Wi-Fi password could be cracked in about 2 hours with a worst-case scenario of around 4 hours, as demonstrated below.
Figures 4 and 5 respectively show the attack scheme and the results of the cracking attempt on one of the vulnerable DJI drones (in this case a DJI Mini Pro 3). It took around 2 hours to crack the password using a single Nvidia T4 GPU hosted on a cloud server instance generated on the fly. The Wi-Fi password for the drone under attack is df46c50a.
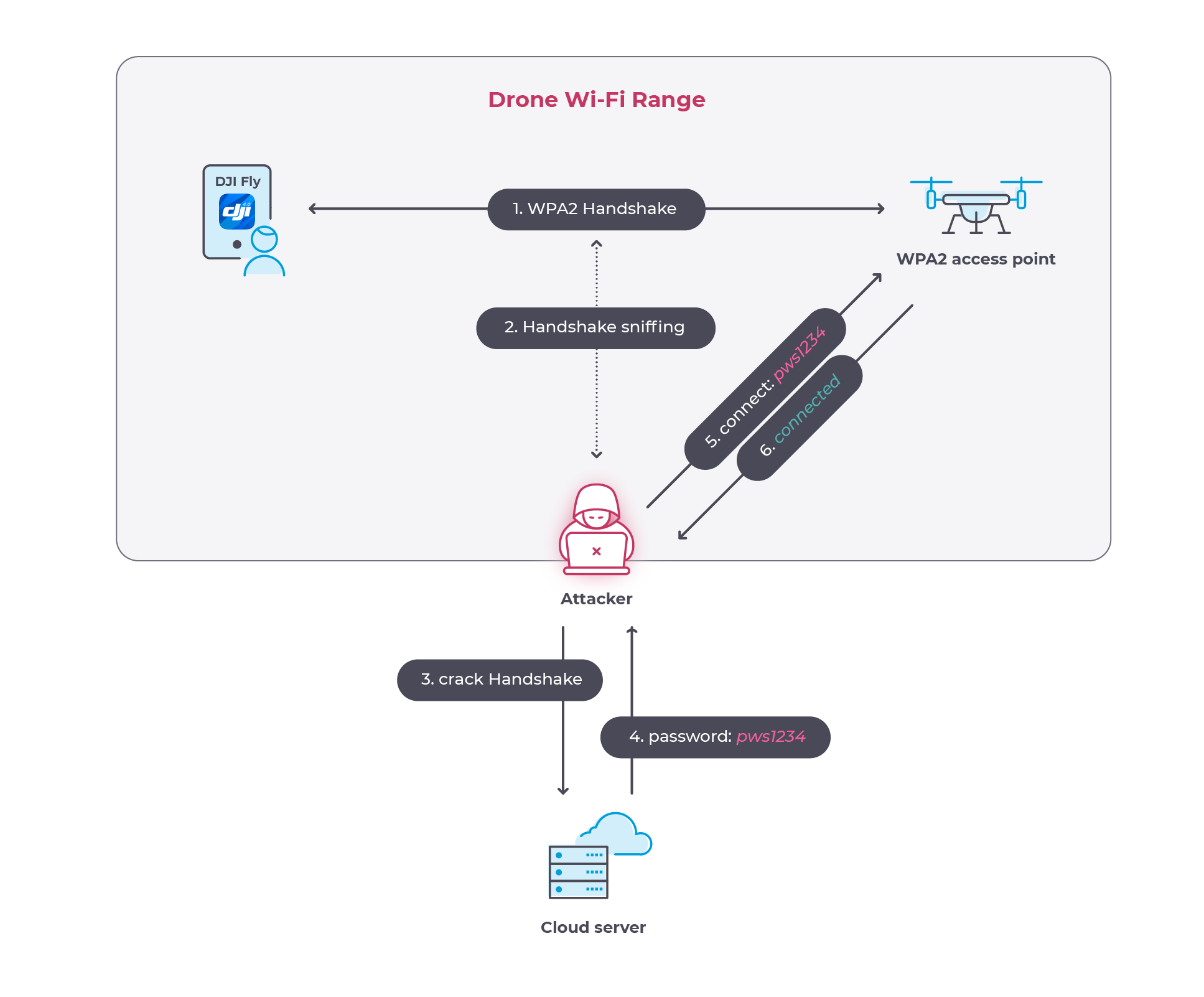
The CVE ID assigned to the vulnerability is CVE-2023-6951 with a CVSS score of 6.6 (AV:A/AC:L/PR:N/UI:R/S:C/C:H/I:N/A:N - MEDIUM). By exploiting this issue, an attacker positioned within the range of the Mavic 3 Wi-Fi network could establish a connection to the drone without any authorization. Subsequently, the attacker could interact with the drone, potentially executing additional vulnerabilities to compromise its security.
The FTP Service
One of the attack surfaces examined during our research was the FTP service operating on the drone, granting access to encrypted diagnostic data without requiring authentication. By fuzzing the service running it on an Android emulator, a persistent denial-of-service attack was discovered, triggered by a malformed SIZE request. Rectifying this issue necessitates rebooting the drone device to properly restart the service.
Given that the FTP service is intended solely for diagnostic purposes, its availability may not be considered highly impactful and despite assigning a CVE to this vulnerability (CVE-2023-6950) and a CVSS score of 3.0 (AV:A/AC:L/PR:L/UI:R/S:U/C:N/I:N/A:L – LOW), DJI opted not to address it. The rationale behind this decision is that the service is exclusively for diagnostic purposes, offering access to encrypted data only. Consequently, the vulnerability has been categorized as 'disputed'.
The vtwo_sdk Service
The vtwo_sdk daemon service is instantiated through the /system/bin/dji_vtwo_sdk binary file. This service likely serves maintenance purposes and its significance as an attack surface stems from its execution with elevated privileges (root) as shown in Figure 6 and its engagement in listening on port 10000 for TCP connections.
This renders it susceptible to external attacks, whether from a malicious application installed on the mobile phone utilizing QuickTransfer Mode or an intruder connected to the drone's Wi-Fi network authorized or not, exploiting the previously described vulnerability to retrieve the randomly generated password (CVE-2023-6951).
The service is built upon a custom TLV-based protocol (Type-Length-Value) over TCP to process external input commands. In an effort to identify vulnerabilities within this protocol, we subjected it to analysis on the Android emulator. To explore potential security issues, we initiated a simple fuzzing campaign designed to uncover corner cases that could expose security vulnerabilities. Figure 7 shows the service running on the emulator during the fuzzing campaign.
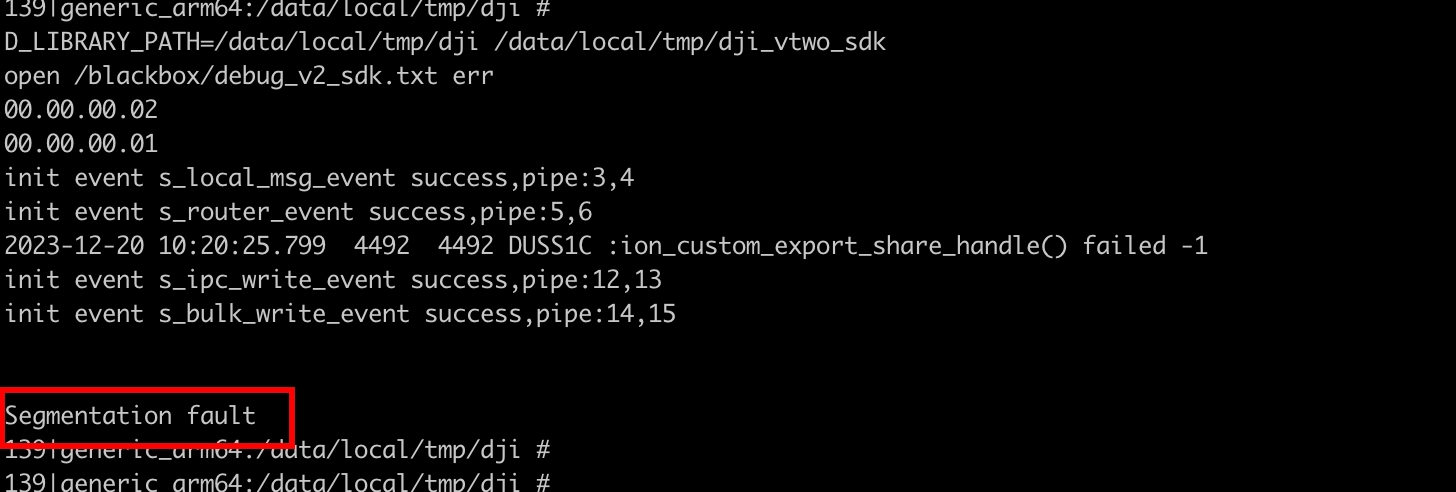
Consequently, we identified six distinct crashes, with three of them exploitable solely for a denial-of-service attack (CVE-2023-6948, CVE-2023-51452, CVE-2023-51453), attributed to a sanity check enforced by the Android FORTIFY security feature. For these vulnerabilities, a CVSS base score of 3.0 has been assigned (AV:A/AC:L/PR:L/UI:R/S:U/C:N/I:N/A:L – LOW).
The remaining three crashes encompassed two Out-Of-Bound Write issues and an Array-Index-Out-Of-Bound vulnerability. Depending on the attacker's proficiency, these primitives could potentially result in arbitrary code execution or information leaks, eventually resulting in the complete compromise of the drone, thanks to the elevated privileges granted to the vtwo_sdk service.
For these three vulnerabilities (CVE-2023-51454, CVE-2023-51455, CVE-2023-51456), a CVSS score of 6.8 (AV:A/AC:H/PR:L/UI:R/S:U/C:H/I:H/A:H – MEDIUM) has been assigned.
The HTTP Service
The final attack surface taken into account is the HTTP service operating on port 80, accessible from the mobile device connected through QuickTransfer. Upon analyzing the firmware image's init scripts, it was determined that this service is implemented in the binary file /system/bin/dji_http_server.
Through reverse engineering of the binary, it was discerned that the HTTP service incorporates an unauthenticated API, enabling the scanning of the drone's memory and the download of pictures and videos from it. The absence of authentication between the DJI Fly application and the HTTP server on the drone renders the API susceptible to abuse, allowing unauthorized exfiltration of media from the drone.
In light of these concerns, a Missing-Authentication-For-Critical-Function vulnerability has been brought to the attention of DJI to address and secure this functionality.
More in detail the HTTP API can be invoked in this way: v2?storage=[storage_id]&path=[file_path]
where:
- storage: a choice between 0 and 1, specifying the internal or external (sdcard) drone memory
- file_path: the path of the media file to be downloaded, relative to the selected storage
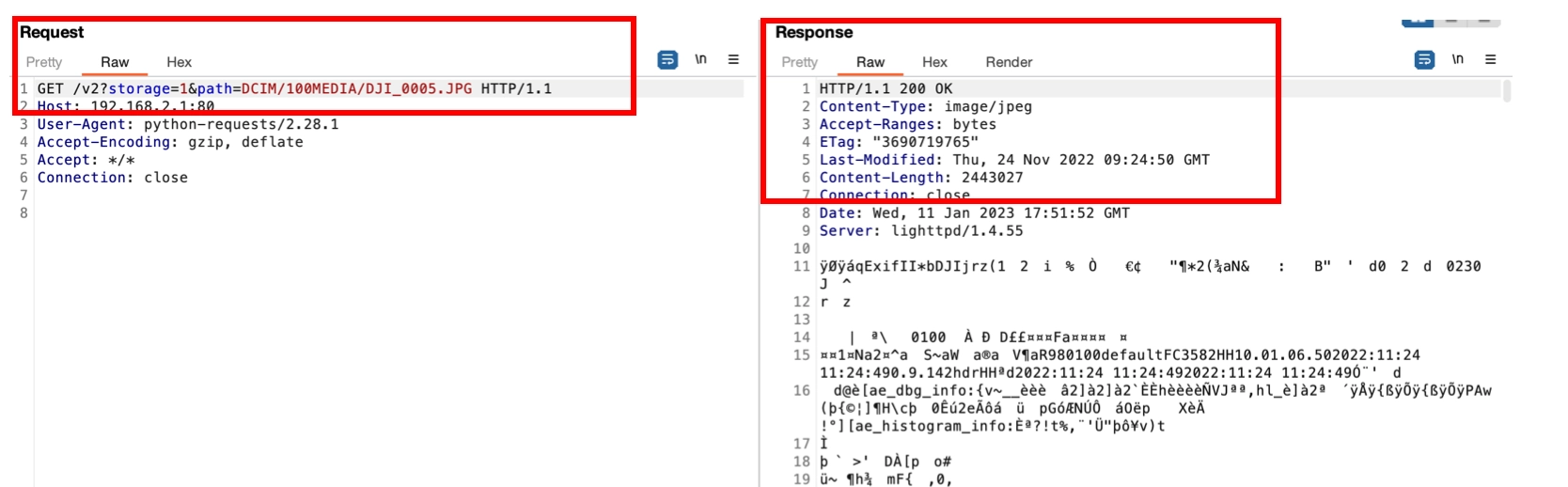
Since generated file names have a standard format when saved on the memory (DCIM/100MEDIA/DJI_xxxx.JPG or DCIM/100MEDIA/DJI_xxxx.MP4 where xxxx is an incremental number) it is possible to guess the file name and download photos and videos in an unauthorized way (e.g. using a python script brute-forcing the file name paths). An example of an HTTP request that can exfiltrate data from the drone (192.168.2.1) is:
GET/v2?storage=1&path=DCIM/100MEDIA/DJI_0005.JPG HTTP/1.1
Host:192.168.2.1:80
User-Agent:python-requests/2.28.1
Accept-Encoding:gzip, deflate
Accept:*/*
Connection:close
Figure 8 shows how an unauthenticated request on the drone static ip address (192.168.2.1) requesting the file DJI_0005.JPG succeeds.
Exploiting the previously mentioned vulnerability related to the weak random Wi-Fi password generation (CVE-2023-6951), an attacker could connect to the drone and abuse this API (Figure 9a). Furthermore, a malicious application installed on the mobile device using QuickTransfer could silently exfiltrate pictures and videos from the drone without requiring any privileges except for internet access (necessary for performing HTTP requests) as shown in Figure 9b.
.webp)
The vulnerability is officially identified by the CVE ID CVE-2023-6949, accompanied by a CVSS score of 5.2 (AV:A/AC:L/PR:L/UI:R/S:U/C:H/I:N/A:N - MEDIUM). However, its status is marked as 'disputed' as DJI does not acknowledge it as a security issue. The rationale behind this decision is rooted in the belief that rectifying the weak Wi-Fi password generation (CVE-2023-6951) would eliminate the remote attack vector. Additionally, any potential compromise of a mobile device is considered the user's responsibility.
Assessing and Managing Risk
The use of drones is becoming increasingly widespread and serves various purposes. DJI, holding over 90% of the market share, stands as the leading provider. Given the extensive adoption of their devices, particularly in professional settings, ensuring the security of DJI drones is paramount.
We strongly encourage users to promptly upgrade their devices to the latest firmware versions, thereby safeguarding their data from potential security risks of the nine identified vulnerabilities that have the potential to facilitate unauthorized exfiltration of videos and pictures by exploiting the QuickTransfer Mode Wi-Fi protocol.
Organizations operating any type of drone should also consider how these operations and connected applications may be affected by a cyberattack. If functions within a drone were compromised, how would that change the risk exposure during a given operation? For example, what if lighting could be turned on or off during surveillance or monitoring work?
For devices which offer functionality such as passing operations from one operator to another, what might be the outcome if an unauthorized operator was able to take control of the device? Could this happen accidentally during an operation where multiple drones were operating with multiple operators?
All drone operators are required to give consideration to the locations they operate in, and it is wise to consider how the risk profile changes if a sudden loss of control is experienced, especially at scale. When considering data privacy, operators should consider how to manage risks associated with unauthorized access to video or imagery. A worst-case scenario could be exfiltration of sensitive footage which compromised a wider operation and led to an unexpected change in risk profile.
Drone hardware, the associated firmware and software, should not be the only focal point when assessing and evaluating risks. Other devices, procedures and processes within a drone operator’s environment may be vulnerable to attacks that expose or expand an attack surface. Organizations must consider the wider infrastructure when assessing the risks to drone operations.
At the same time, organizations should also consider how the operation of third-party drones could affect their business and operational risk. We have already seen examples of airport operations being interrupted by unauthorized ingress of drones. Risk management and security leaders should consider how such an intrusion would affect their operations and what mitigations may need to be implemented to control and manage these risks.









