On the heels of a June 7th CISA #StopRansomware advisory covering the CL0P ransomware gang’s exploit of a vulnerability in the MOVEit file transfer app, CL0P took center stage in press coverage last week when it published a “leak site” naming dozens of victims in the US, Germany, Belgium, Switzerland and Canada. While news outlets were quick to hype a list of government agencies and critical infrastructure organizations who were impacted, in this blog we’ll cover what OT and critical infrastructure organizations should know about CL0P and what they can do to ensure they’re not a victim.
Who is CL0P?
First discovered in 2019, as a variant of the CryptoMix ransomware family, the CL0P ransomware gang (also known as TA505) started with a large-scale spear-phishing email campaign and has since gained a reputation for its constantly changing tactics, techniques and procedures (TTPs). Over the years, the Ransomware as a Service has been used to successfully exploit IT vulnerabilities to extort hundreds of millions of dollars in payouts from high-profile organizations and government agencies around the world. Starting in 2020 the group began focusing on zero-day vulnerabilities in legacy file transfer apps.
According to publicly available information, beginning May 27, 2023, CL0P began exploiting a previously unknown SQL injection vulnerability (CVE-2023-34362) in MOVEit Transfer, a managed file transfer (MFT) solution from Progress Software. This vulnerability was added to CISA’s Known Exploited Vulnerabilities (KEVs) catalog on June 2nd. Internet-facing MOVEit Transfer web applications were infected with a web shell named LEMURLOOT, which was then used to steal data from underlying MOVEit Transfer databases. CL0P then posted a message on their .onion website urging organizations who were using MOVEit Transfer at the time of the attacks to get in touch with them to arrange payments in order to prevent the public exposure of sensitive company information.
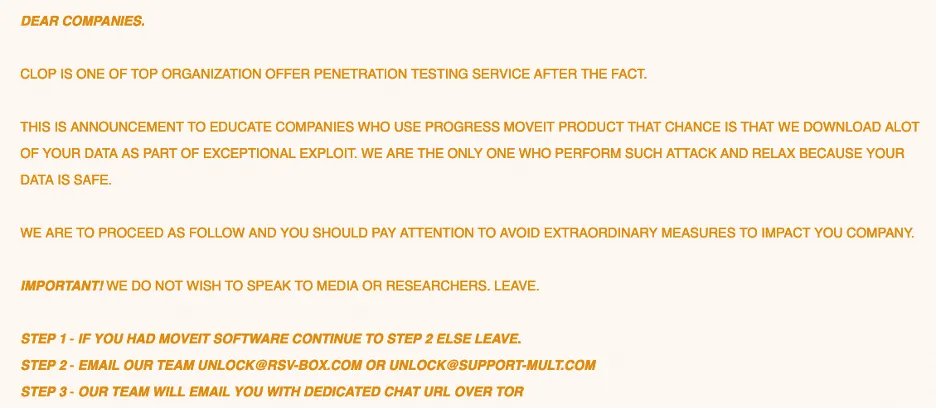
What To Do If You Use MOVEit
In its June 7th advisory – updated June 16th, CISA advises organizations who use MOVEit to immediately:
- Take an inventory of assets and data, identifying authorized and unauthorized devices and software.
- Grant admin privileges and access only when necessary, establishing a software allow list that only executes legitimate applications.
- Monitor network ports, protocols, and services, activating security configurations on network infrastructure devices such as firewalls and routers.
- Regularly patch and update software and applications to their latest versions, and conduct regular vulnerability assessments.
What Should Critical Infrastructure Organizations Do About CL0P?
While some critical infrastructure organizations appear to have been impacted by this latest CL0P activity, they are not being directly targeted by the CL0P gang. While this is an opportunistic attack, these latest exploits are a reminder that as the IT and OT worlds converge and become increasingly interdependent, practices must be in place to strengthen both security defenses and resiliency against cyber criminals.
In order to minimize the impact of technique T0819: Exploit Public-Facing Application, it is important to not only decrease the publicly exposed services to the absolute minimum, but to additionally assume that any publicly exposed service can potentially be compromised using an exploit for a publicly unknown vulnerability. In addition to regularly updating software and scanning for vulnerabilities, a threat model should assume that attackers will eventually come up with a method to compromise a publicly exposed service. Some of these attempts can be thwarted by preventing malicious payloads from reaching their target using technologies like Web Application Firewalls (M0950: Exploit Protection). However, organizations should also assume that these technologies may also be bypassed and focus on limiting the options that a successful attacker has when it moves laterally. Network segmentation (M0930: Network Segmentation) of internet-facing hosts can restrict the options that an attacker has. If strict network segmentation is not possible, which is the case when it comes to software providing centralized resource management, it is important to quickly detect and contain attackers.
The movements of attackers who have successfully breached a network can be detected as they attempt to understand the network they are in and move laterally through it to extract sensitive information to be used for extortion attempts. With network and host monitoring in place, operators will be alerted of this unusual movement and can minimize the impact of a breach or stop its tracks early on.
Added Protections for Nozomi Networks Customers
Customers using a current version of the Nozomi Networks Threat Intelligence service will automatically receive the latest detections and indicators of compromise for the campaigns mentioned above. Specifically, we provide detections for network infrastructure used by CL0P for the MOVEit and GoAnywhere campaigns and for malware samples such as TrueBot, LEMURLOOT and others used by the group.
Detections can be found in the following files:
- ENTERPRISE_WEBSHELL_Generic_Aspx-MOVEit.yar.content
- ENTERPRISE_WEBSHELL_Generic_Aspx-MOVEit_2.yar.content
- ENTERPRISE_EXPLOIT_Generic_MOVEit-ioc.json.content
- ENTERPRISE_RANSOMWARE_(TA505)Generic_CL0P.json.content
- ENTERPRISE_DOWNLOADER_(TA505)Truebot_samples.json.content
- ENTERPRISE_WEBSHELL_(TA505)LEMURLOOT_samples.json.content
- ENTERPRISE_RANSOMWARE_(TA505)Fortra-GoAnywhere_January-June-IPs.json.content
- ENTERPRISE_RANSOMWARE_(TA505)MoveIt_June-May-IPs.json.content
Additionally, customers should use the information provided by the Vulnerability Assessment subsystem of the Threat Intelligence package to ensure that they are not running vulnerable versions of the software exploited by CL0P.
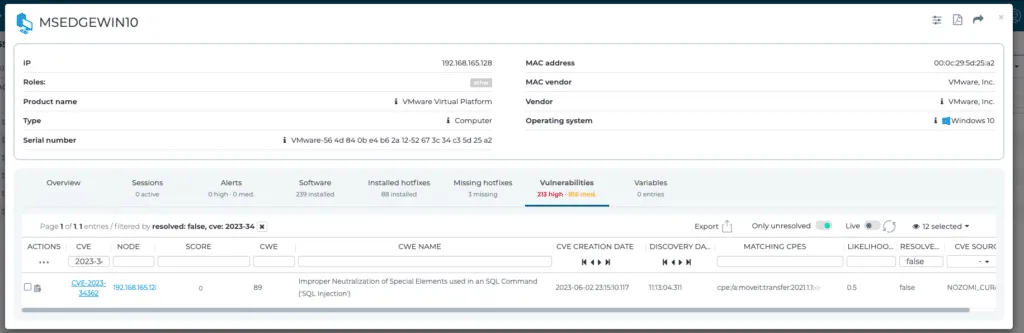
As more details about CL0P’s campaigns unfold, the Nozomi Networks Threat Intelligence team continues to monitor the situation and is dedicated to providing updates in the form of new Threat Intelligence packages, so it is highly recommended for customers to use the latest version available at the time. Additionally, after a successful intrusion, actions taken by attackers can often be detected using anomaly detection, particularly when attackers try to ‘live off the land’, conduct reconnaissance activities, or exfiltrate data.







