Nozomi Networks recently had the privilege of sharing our technical research at the Black Hat MEA 2023 security conference in Riyadh. It was an honor to participate in this event and a testament to our dedication for diving deep into the topics that we're passionate about. Our findings demonstrated how vulnerabilities we found in Mitsubishi Safety PLCs could disable them and cut off network access to legitimate engineers. The consequences could be severe, given that safety PLCs are integral to a system’s ability respond rapidly to potential hazards.
This event is a fresh chapter in the legacy of the Black Hat series, which has been a cornerstone in the cybersecurity world for many years. This was like ticking off another goal for us, as we've been around the block presenting at our work at events like Black Hat USA, S4, DEFCON, and more. Over the years, Black Hat MEA has established itself as the leading cybersecurity event within the Middle East and Africa region, bringing together industry leaders, experts, and enthusiasts to share knowledge and explore cutting-edge technologies. The event is now in its third edition, gathering over 25,000 attendees.
Our Research: Zero-Day Vulnerabilities Affecting Mitsubishi Electric Safety PLCs
Our Black Hat MEA highlight was the opportunity to share our latest research. Nozomi Networks security researcher Andrea Palanca presented 8 zero-day vulnerabilities found in the Mitsubishi Electric MELSOFT protocol, which affect the safety PLC line of the Mitsubishi Electric MELSEC iQ-R series.
In comparison to a standard PLC, safety PLCs are designed with a primary focus on implementing safety functions to prevent accidents and protect personnel, equipment, and the environment. They are programmed to monitor and control safety-critical processes, such as emergency stops, machine guarding, and personnel protection systems.
The significance of safety PLCs lies in their ability to respond rapidly to potential hazards, initiating protective measures or shutdowns in real-time to mitigate risks. The vulnerabilities discovered by Nozomi Networks Labs would have allowed an unauthenticated attacker to arbitrarily induce failures in the protection logic executed by these devices. These vulnerabilities could simultaneously cut off network access to all legitimate engineers, leaving them with no other option than to physically access the device to reset it.

During this presentation, we disclosed the undocumented implementation details of the authentication and authorization schemes in the Mitsubishi Electric-proprietary MELSOFT protocol for the first time. These details were acquired through extensive reverse engineering efforts on an iQ-R R08SFCPU. Below, We detailed all the vulnerabilities discovered by Nozomi Networks Labs and showed extracts of packet captures and/or scripts to precisely pinpoint the underlying cause. For more information on these vulnerabilities, please refer to our two blogs: the first focusing on the five flaws affecting the MELSOFT protocol, and the second covering three loopholes on GX Works3 project files.
We didn't confine our study to a purely theoretical stance: we showed two practical demos of how, by chaining these vulnerabilities, an unauthenticated attacker may tamper with the execution of the safety routines offered by the device while simultaneously preventing any restore attempts through the network by legitimate engineers. These demonstrations were recorded in our Production Line demo, which is a realistic representation of a real-world production facility built in our research headquarters in Switzerland.
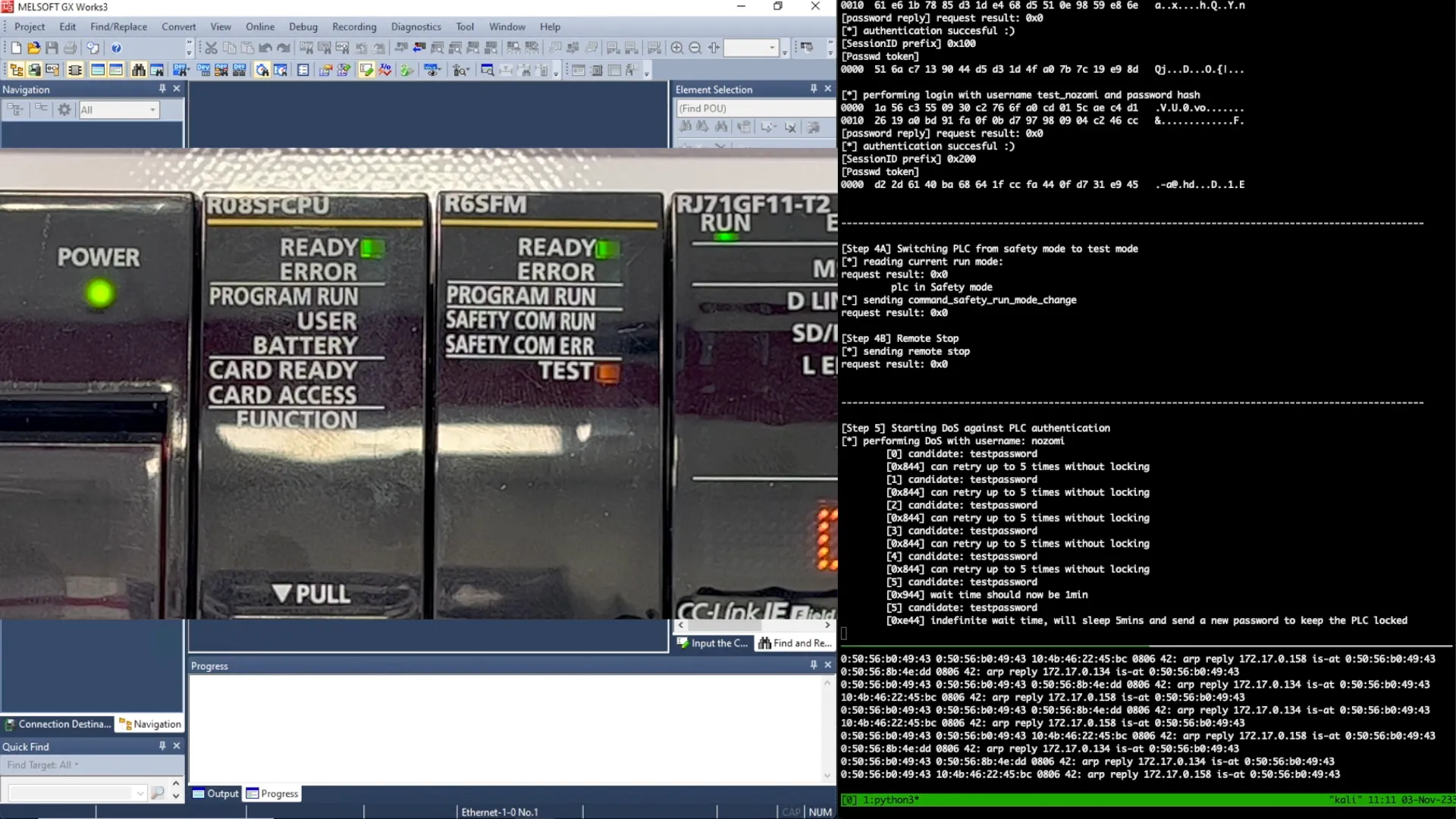
We concluded our talk by sharing officially developed patches and, for all vulnerabilities that are not fixed yet, actionable mitigations that can be enacted. Notably, we released for free a version of our internal Wireshark dissector of the MELSOFT protocol, specifically designed to help security teams to investigate these issues in autonomy, and some PCAPs of the presented attacks. Those can be downloaded from our GitHub repository.
As we reflect on the enriching experience and valuable connections made during the Black Hat MEA security conference, we would like to extend our sincere appreciation to Tahaluf (an Informa business) and the Saudi Federation for Cybersecurity, Programming & Drones for their integral roles in making this conference a highlight of this cybersecurity calendar, and, we are confident, for many years to come.









